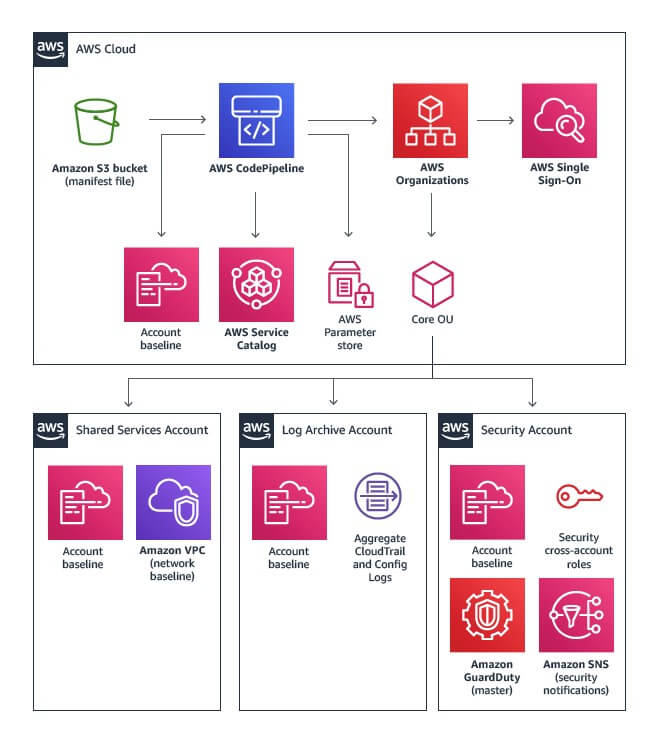
Landing zone is a new solution by AWS, it is used to build a scalable, secure multi account AWS environment. Building a multi account the traditional method takes a significant amount of time and effort, especially when reaching a baseline security configuration and other features such as turning on AWS Config, AWS Inspector, AWS GuardDuty, setting up VPCs etc. Landing zone helps setting up multiple accounts with a baseline for security and other features available in AWS and hence significantly reduces time and effort spend to create these accounts and subsequent new accounts within the same organization.
Figure 1: Landing zone overview (Image courtesy: AWS)
Reaching the Landing zone pattern involves configuring and enabling a slew of AWS services and settings to reach the baseline requirement.
Here are the various categories of baselines required, they are:
- Account security baseline
Account baseline involves turning on the following:
- Global AWS CloudTrail for every account and enable sharing these logs to the log archive account and save a local copy of CloudTrail in each account.
- Enable log integrity and bucket encryption.
- Enable AWS Config and rules.
- Send config and configuration logs to the log archive account.
- Enable IAM password rules.
- Create audit and admin IAM account/roles
- Setup GuardDuty and send events to log archive account.
- Logging baseline
Logging baseline involves the following:
- Act as a central logging location.
- Act as a single source of truth with limited read only access.
- Integrate with various logging solutions like Splunk, Sumo Logic, ELK or our very own stackArmor ThreatAlert or stackArmor OpsAlertsolutions.
- Data security baseline
Logging baseline involves the following:
- Enable and configure Config rules for monitoring s3 data encryption, EBS encryption etc
- Automate policy-based data security for multiple AWS account by using
- Provide notification on specific CloudTrail and config events such as someone opening port 22 to the public etc.
The above baselines ensure that the accounts created by the landing zone pattern meet the minimum AWS security configuration.
Now that we understand what a – Landing Zone pattern’ entails, let us look at the ways to get there:
- Using AWS’s Landing zone: The Landing zone service deploys the entire stack including all the core accounts and an account vending machine (AVM) which is used to deploy further accounts needed for your actual application. This solution deploys all the baseline components without an option to pick and choose. Landing Zone is a not a native service is only available through AWS professional services or through AWS partners.
- Using AWS Organizations: Another way to achieve the landing zone pattern is to use organizations and service control policies (SCPs) to deploy policies to match the landing zone pattern. This requires a more hand on approach to the landing zone service.
- Using AWS Control Tower: AWS Control Tower is a native service with predefined blueprints and guardrails to reach a pattern like the Landing Zone pattern with more services such as AWS SSO enabled.
- Using AWS CloudFormation: The final and the most tedious and hands on approach is to use CloudFormation scripts to enable the services and to create your own accounts.
Some of the key differences between AWS Landing Zone and AWS Control Tower are flexibility and availability. AWS Control Tower is a native service but is currently only available in 4 regions as of the time of writing this blog. Another major drawback of using Control Towers is the flexibility aspect, for example for the SSO solutions, Control Tower deploys AWS SSO by default and there is no way to change that. In case of Landing Zone you can pick and choose your solution, for example for SSO you can go with AWS SSO, Okta , Duo etc. Furthermore, AWS is currently working on a solution that lets users migrate their existing Landing Zone solution to Control Tower. We recommend using Control Tower if you are planning to deploy hundreds of accounts, otherwise its easier and more manageable to stick to one of the other solutions.
stackArmor is excited to be working with security and compliance focused customers looking to implement FedRAMP compliant cloud solutions that help reduce the time and cost by using pre-defined solution architecture components. Contact us to learn more.
Learn more about our FedRAMP compliance solutions by visiting our ATO on AWS solutions page at https://stackarmor.com/solutions-2/devops/