Market research firm Forrester forecasts that nearly 60% of North American enterprises rely on public cloud computing platforms. Clearly, businesses are realizing business value from faster delivery speeds — but as an old adage goes speed thrills but kills! If DevOps has helped accelerate development and deployment cycles, then it is critical for security and compliance processes to keep pace. Managing digital risk in an age of agile, devops and cloud is complicated. Constant configuration changes, code & container vulnerabilities, cloud sprawl, new compliance requirements and scarce talent make the task especially difficult and challenging. McAfee Cloud Adoption & Risk Report estimates that Enterprise organizations have an average of 14 misconfigured IaaS/PaaS instances running at one time, resulting in an average of 2,269 individual misconfiguration incidents per month.
Vulnerability Management at scale with DevSecOps
Clearly the security and compliance functions must keep pace with such rapid change. The ability to provide end to end security from “code to cloud” using continuous scanning and monitoring is the only way to ensure the confidentiality, integrity and availability of digital assets. The cloud automation, security and compliance experts at stackArmor have developed a comprehensive framework based on OWASP, CIS and NIST standards to develop a foundational security framework for DevSecOps. The framework is codified in the stackArmor ThreatAlert DevSecOps solution delivered as a fully managed service.
Vulnerability management in code
Performing code analysis is critical to ensure that security vulnerabilities are caught at the earliest possible part of the SDLC.
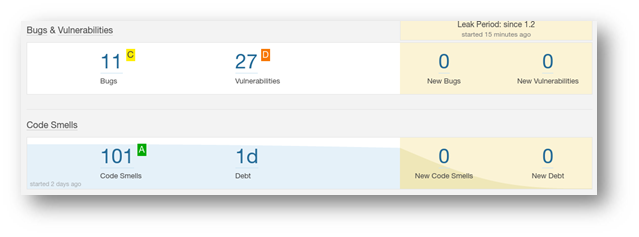
The code scan helps identify specific code vulnerabilities. A recent code scan performed on a ruby and php based healthcare application revealed the use of MD5 as a hashing algorithm. This is a weakness and should be remediated.
Vulnerability management in containers
The increasing use of containers requires continuous monitoring and scanning of Docker container images prior to their deployment. stackArmor’s ThreatAlert DevSecOps framework utilizes industry leading tools including acnhore, Docker Threat Registry and TrendMicro Deep Security for as part of the automated tool chain.
Vulnerability management in cloud
Cloud services like AWS are policy driven computing platforms that offer strong capabilities for hardening and secure hosting. However it is critical to continuous monitor and test these policy configurations on a continual basis. The screenshot from stackArmor ThreatAlert’s Unified Threat Portal shows the violation of password policies based on CIS security benchmarks
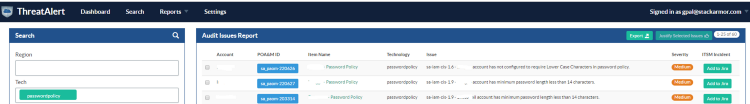
The strong continuous monitoring of such policies help detect to vulnerabilities using DevSecOps tools and thereby reducing digital risk for organizations. Are you interested in learning more about how DevSecOps can help you reduce digital risk? Learn more by reading about stackArmor ThreatAlert or contact us for a free demo.

