Meeting complex government cybersecurity requirements for highly regulated industries can be challenging. Developing a dedicated authorization boundary that places strict security controls on sensitive data helps reduce the time and cost of delivering secure and compliant services. stackArmor has developed a zero-trust architecture that separates application data from security operations with strong identity and monitoring controls.
Continuous monitoring of systems in a holistic manner is a critical requirement as cyberattacks continue to increase. Most Chief Information Security Officers (CISO) and Information Security professionals are rapidly evolving their compliance-centric approach to more proactive logging, monitoring, and alerting posture. This requires a holistic solution that covers the “full-stack” starting with the user and includes the application, data, infrastructure covering both internal and external threat vectors. This blog post gives an insight into our Security Operations Center (SOC) capability for meeting FedRAMP, FISMA, and DFARS compliance requirements.
NIST SP 800-53 provides a ready set of security requirements for FedRAMP, FISMA, and DFARS compliance related to continuous monitoring. stackArmor has successfully helped organizations accelerate compliance with continuous monitoring requirements by developing a standardized platform that can be tailored to meet specific requirements.
The infographic shown below demonstrates a typical deployment architecture for monitoring cloud-based applications. The Landing Zone pattern is a critical enabler for implementing separation of duties and allowing for the deployment of a Cloud GSS that provides robust continuous monitoring to all of the applications.Â
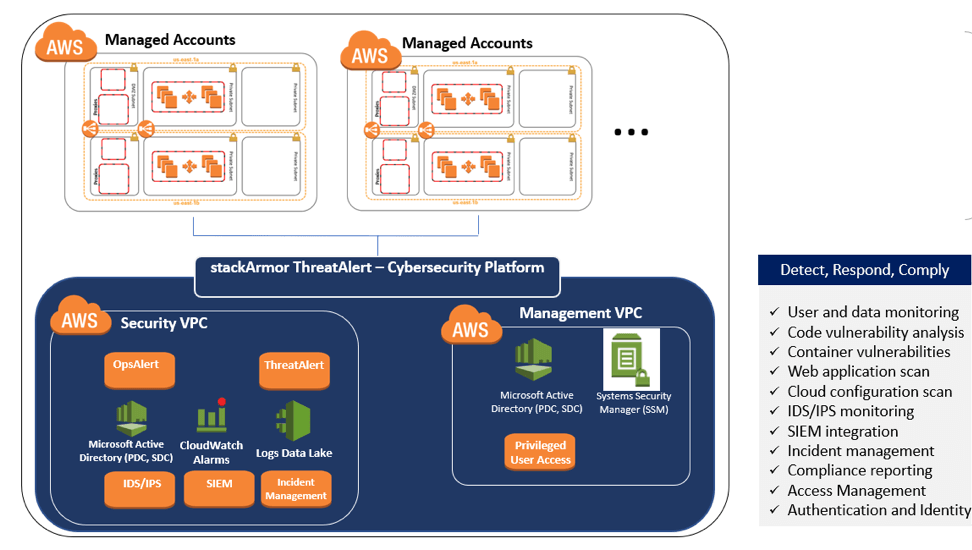
stackArmor ThreatAlert(R) Cybersecurity Platform for meeting NIST SP 800-53 requirements using a Landing Zone architecture pattern
The use of a platform-centric view towards providing a common set of security services is essential to provide cost savings and deliver the “cloud dividend”. A key part to deploying a robust SOC capability is to ensure full-stack coverage. stackArmor has developed their SOC platform to include users, cloud, containers and data. The diagram below demonstrates the coverage of various layers and security services.
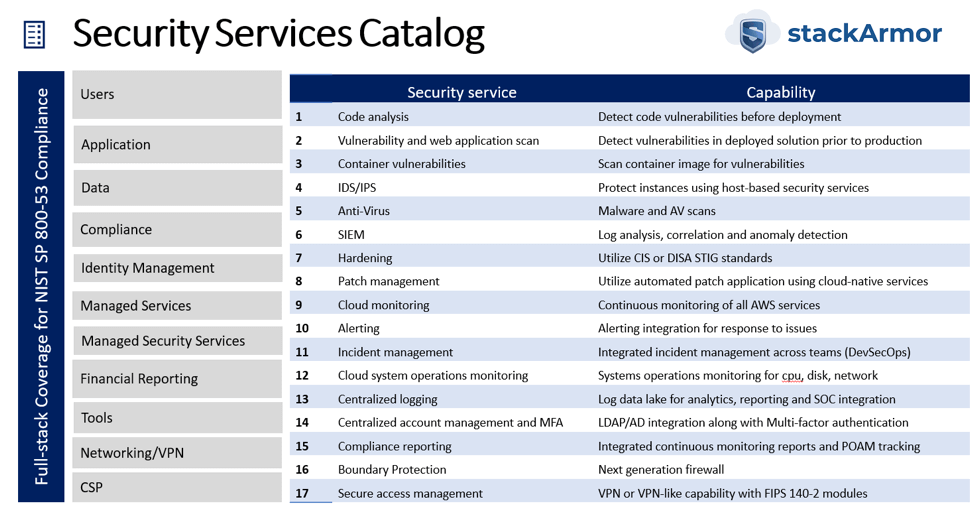
stackArmor’s cybersecurity platform provides a robust set of security services that must be included for compliance with NIST SP 800-53 for FedRAMP, FISMA, or DFARS.
The stackArmor Security Operations Center (SOC) and Continuous Monitoring capability is embedded into the Cloud GSS (General Support System – is a term used in NIST RMF centric environments) for meeting the specifics of NIST SP 800-53 control requirements.Â
Every dedicated SOC and Continuous Monitoring Platform must pay special attention to the following architectural elements:
- A centralized data lake for collecting logs
- Analytics toolsets for correlation, dashboarding and alerting
- Scalability using a hierarchical deployment model
Most SOC & ConMon architectures especially for cloud deployments tend to take a simplistic view of a “single” central SOC. This approach is not inherently scalable as the environments multiple and the cost associated with moving “around” starts to add up. Instead, a more thoughtful Distributed Zero-trust architecture for SOC & ConMon allows for various tiers of SOC data/analysis to be performed avoided overly large collection of centralized security data. The infographic below demonstrates how large organizations especially US Federal agencies should consider architecting their security monitoring capabilities. One might have large programs with their own ability to implement monitoring and security, however, a downstream SOC may monitor the upstream applications by feeding necessary log information.Â
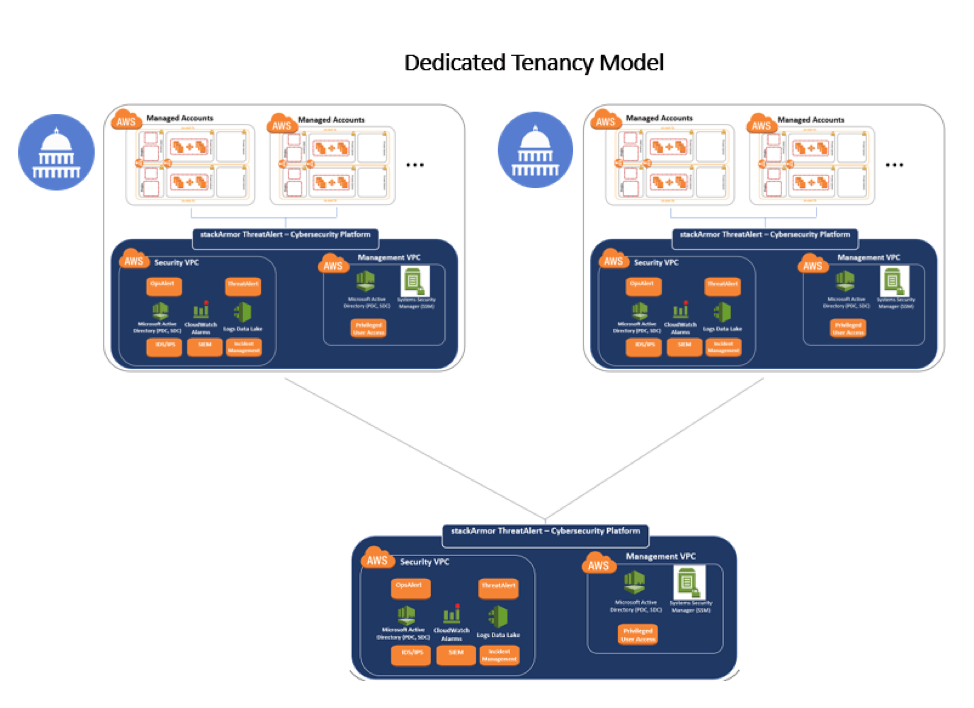
stackArmor SOC architecture that utilizes a hierarchical pattern to implement a SOC of SOC’s pattern to allow for scalability and catering to the unique use cases of Federal Agencies with diverse and distributed cloud deployments managed by a wide variety of teams and vendors.
Are you interested in learning more about our Security Operations Center capability for meeting FedRAMP, FISMA, and DFARS compliance requirements? If you are interested in learning more about our SOC solutions, please contact us for a free consultation. Also do read about our stackArmor ARM methodology for cybersecurity risk management here.Â
About stackArmor :
stackArmor is a provider of Cloud Advisory, Cloud Implementation, and Cybersecurity and Compliance services for healthcare, financial services, and public sector customers. As an AWS Authorized Reseller, AWS Public Sector Partner, and AWS GovCloud competency holder, stackArmor specializes in delivering secure and compliance-oriented AWS solutions, including cloud strategy, platform architecture, DevOps implementation, migration services, managed services and managed security services. Our experts help protect you from the cyberthreat challenges through systems engineering best practices developed over decades while working with US government agencies that require compliance with ISO 27001, NIST, FFIEC, FISMA, FedRAMP, DHS and DISA standards.



