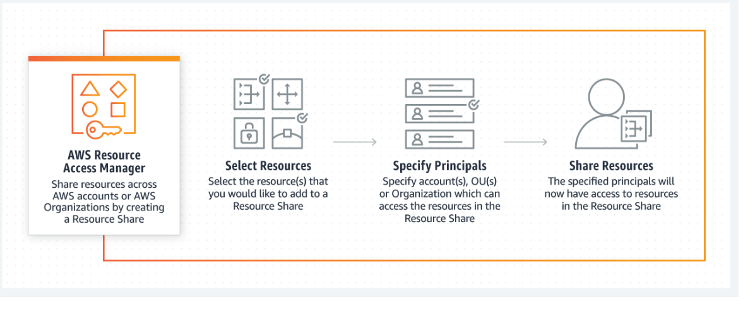
AWS Resource Access Manager (RAM) is a service that enables you to easily and securely share AWS resources with any AWS account or within your AWS Organization. You can share AWS Transit Gateways, Subnets, AWS License Manager configurations, and Amazon Route 53 Resolver rules resources with RAM. RAM facilitates resource sharing between AWS accounts.
Many organizations use multiple accounts to create administrative or billing isolation and to limit the impact of errors. RAM eliminates the need to create duplicate resources in multiple accounts, reducing the operational overhead of managing those resources in every single account you own. You can create resources centrally in a multi-account environment and use RAM to share those resources across accounts in three simple steps: create a Resource Share, specify resources, and specify accounts. RAM is available to you at no additional charge.
AWS Landing Zone best practices dictate the use of AWS organizations to segregate resources in multiple accounts to create administrative, security, and billing isolation, and to limit the impact of errors. The benefits of using RAM in these instances are:
- RAM eliminates the need to create duplicate resources in multiple accounts, reducing the operational overhead of managing those resources in every single account
- You can create resources centrally in a multi-account environment, and use RAM to share those resources across accounts
How stackArmor uses AWS Resource Access Manager
At stackArmor until recently, for most of our customers looking for FedRAMP, FISMA, or CMMC compliant landing zones, we used AWS RAM to share transit gateways launched in the ThreatAlert® General Security System (GSS) account with all other accounts in customer landing zone environments. The use of AWS RAM helped streamline the sharing of subnets from VPCs in other landing zone accounts with the ThreatAlert® GSS account in addition to the transit gateway. The implications are that the ThreatAlert® GSS account can deploy resources directly into those other VPC subnets to reduce data transfer costs between VPCs (through the transit gateway) and allow for cross-account read-only administration tasks while still maintaining a landing zone architecture through account ownership.
Do you have questions about the AWS Resource Access Manager for your FedRAMP, FISMA, or CMMC compliance project? Please contact us by filling out this form.
Author: Matt Selvyn, DevOps Engineer at stackArmor