Continuous monitoring is critical to meeting HIPAA, FedRAMP, FISMA or NIST CSF requirements for ensuring the confidentiality, integrity and availability of digital assets. Splunk is a great product for implementing robust monitoring and management capabilities.
Spunk Universal Forwarder – Yet another agent?
The typical approach to getting data out of an AWS EC2 instance and into Splunk is through the Splunk Universal Forwarder. The universal forwarder gathers data from a data source and sends it to a Splunk deployment. This does require putting another agent on the instance leading to “agent proliferation” and adding additional maintenance overhead. Many security and compliance focused organizations mandate minimizing the number of agents installed on EC2 instances.
Using CloudWatch Agent with HEC
Many organizations want to limit the number of agents for the purposes of security, maintainability and performance. Luckily most organizations allow installing the latest AWS CloudWatch agent. The CloudWatch agent allows the transfer of important data for monitoring to be pushed to AWS CloudWatch.
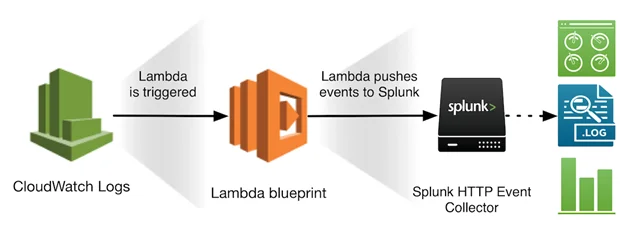
Image: Courtesy Splunk at https://www.splunk.com/blog/2017/02/03/how-to-easily-stream-aws-cloudwatch-logs-to-splunk.html
The ability to pipe log data to AWS CloudWatch logs and then using Splunk’s HTTP Event Collector (HEC) to forward to Splunk’s aggregation engine is an easy way out. HEC enables transmitting log data directly from AWS CloudWatch to Splunk Enterprise. This real-time operational intelligence architecture helps reduce “agent sprawl” and enables powerful security incident and event management for meeting HIPAA, FedRAMP, FISMA and NIST security and compliance standards.

