ISVs and Startups are increasingly being driven to provide software as a service to Government agencies. SaaS solutions are critical to driving digital transformation and helping agencies meet their mission requirements. Commercial organizations must obtain a FedRAMP Authority To Operate (ATO) to ensure that their cloud system meets government data confidentiality, integrity, and availability requirements. The technical architecture for obtaining an ATO can be especially challenging for large multi-product or multi-country organizations. For example, large ISV’s have multiple product lines or complex compliance requirements that must satisfy current and future needs. A platform-centric architecture is essential to ensure that the FedRAMP compliant system is scalable given the high cost of initial compliance.
stackArmor has pioneered ATO Acceleration using an “in-boundary” platform-centric architecture on AWS. stackArmor ‘s ATO Acceleration solution is vetted by AWS and is called ThreatAlert®. The solution incorporates two key best practices highly relevant for compliance-focused organizations: 1) A landing zone pattern and 2) an “in-boundary” deployment of security services. The landing zone provides common security, management, and network services that can be shared among tenant workloads or applications. This pattern helps reduce the cost of the overall solution and allows for multiple product lines or customers to be served through one common accredited platform. “In-boundary” deployment ensures that all data remains within the system boundary.
Large organizations are increasingly looking for “compliance templates” that can be easily replicated and copied from one region to another. This is very important for large ISV’s or Enterprise customers operating in global regions such as the US, Canada, EMEA, and APAC or combinations thereof. Data sovereignty, GDPR, and FedRAMP compliance are just some of the drivers for adopting compliance templates.
ATO Acceleration with Landing Zone-as-Code
ATO stands for Authority To Operate (ATO) which is a phrase generally used to authorize the ability of a system to store and process government data. We at stackArmor however believe that the concept of an ATO applies to any system and organization that is required to meet a specific compliance standard including PCI-DSS, HIPAA, SOC2 or similar. For organizations hosting government data, security requirements for achieving an ATO are described in NIST Special Publication 800-53. Developing systems that comply with these stringent security requirements can be challenging for large organizations looking to meet FedRAMP, ISO, or specific standards like GDPR or Canada’s ITSG-33. Compliance templates such as landing zones especially when expressed in code can reduce the time and cost of compliance. A key first step is to come up with a design or blueprint. stackArmor’s ThreatAlert® landing zone blueprint is an AWS vetted solution for ATO Acceleration. There are other automation techniques and solutions such as AWS Control Tower that help provide orchestration to help realize a landing zone. Every organization must make a determination on the right approach for them based on specific requirements. These requirements could include the need to deploy in various regions, leveraging specific cloud services, cost, and complexity trade-offs.
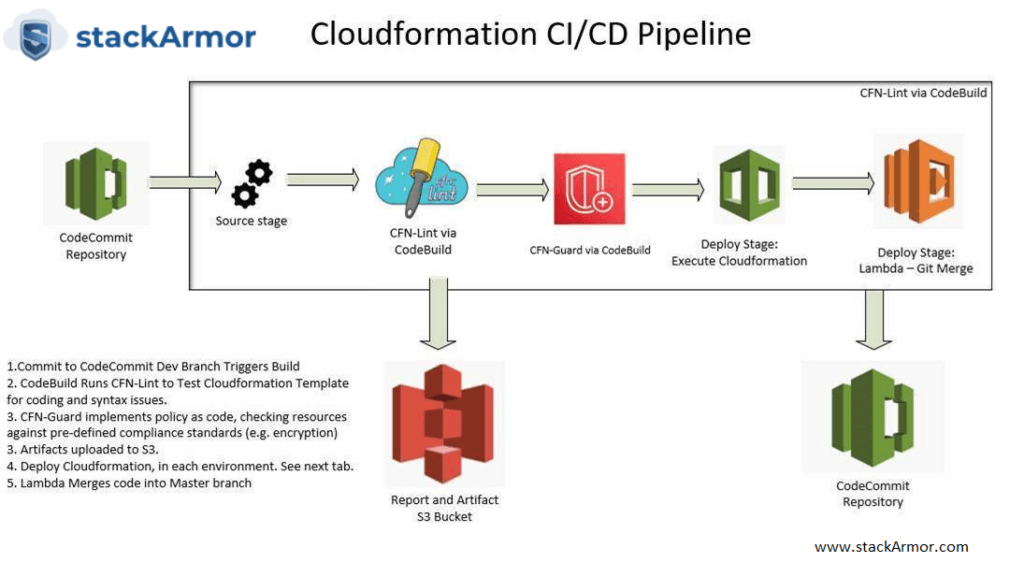
Sound very complicated? Help is on the way – AWS CDK released in 2019 helps simplify the creation of “compliance templates”. AWS Cloud Development Kit (CDK) was launched in July 2019 to accelerate and simplify the adoption of infrastructure-as-code. AWS CDK uses the familiarity and expressive power of programming languages for modeling compliance templates or landing zones (for our use case). It provides high-level components called constructs that preconfigure cloud resources with proven defaults, to provision resources in a safe, repeatable manner through AWS CloudFormation. It also provides support for Terraform using cdk tf for defining Terraform HCL state files in TypeScript and Python. For kubernetes users, the cdk8s project enables the use of CDK constructs for defining kubernetes configuration in TypeScript, Python, and Java. cdk8s can be used to define kubernetes infrastructure running anywhere and can be used with the AWS CDK’s Amazon Elastic Kubernetes Service (Amazon EKS) construct the library. The power of AWS CDK allows us to express our compliance templates using simpler and more streamlined programming abstractions reducing the time and the aggravation associated with developing large complex cloudformation templates. The use of AWS CDK allows us to truly implement infrastructure as code and implement DevSecOps at the foundational level and shift security and compliance to the left. The infographic below provides an overview of a CI/CD pipeline with in-built quality and security checks:
Have questions? Click here to contact us and our Cloud Solutions Specialist will get in touch with you shortly!
Author: Matthew Venne, Director of Solutions Architecture at stackArmor



