As more and more businesses are hosted online and increasingly on cloud platforms such as AWS, it is critical to ensure robust cybersecurity defenses are in place. Typically, the security architecture for most web facing applications begins with boundary protection using a firewall. There are a number of security sub-systems such as Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS) and Web Application Firewalls (WAF) which are generally considered as basic requirements. This is especially true for online businesses offering services in the Healthcare, Financial, Government and Commercial payments market.
As always there is a wide variety of choices and it is critical to understand the role of each one of the security systems to make an informed implementation decision. Let us begin by reviewing some of the basic definition on what these system do and the protections they provide.
Intrusion Prevention System (IPS) – An IPS is an appliance that monitors and analyzes network traffic to detect malicious patterns and potentially harmful packets. Typically, most IPS offer firewall, unified threat management and routing capabilities. There are numerous advances in IPS technology with a sophisticated set of capabilities including in-line deep packet inspection, intrusion prevention through rules & signature detection, application inspection and control, SSL/SSH traffic inspection, website filtering and quality of service/bandwidth management. While there are many products in the marketplace, a common example of such a solution is Fortinet’s FortiGate product.
Web Application Firewall (WAF) – A WAF is typically an appliance or service that is used to secure your web sites/applications against threats like DoS, Cross Site Scripting, and SQL injection, etc. The WAF appliance is positioned before the web server. Typically, a WAF provides the ability to configure security rules and conditions through a web ACL (access control list) that detects and prevents malicious requests from being processed by the web server. Given the need for performance many SaaS and online business providers use Content Delivery Networks (CDN) such as AWS CloudFront or Akamai which offer integrated WAF capabilities. An example of a standalone product is Fortinet’s FortiWeb product. The diagram below shows a typical WAF configuration in a AWS VPC.
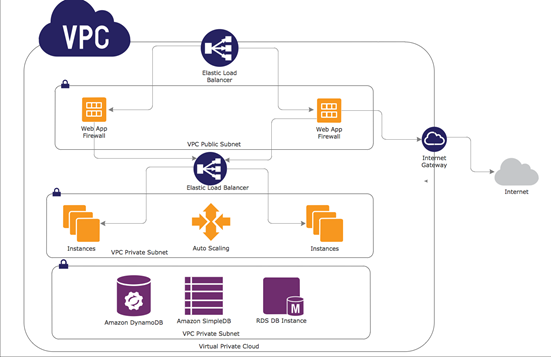
Figure 1: Diagram showing WAF deployment within a AWS VPC
It is important to note that the diagram provides a highly simplified diagram. Generally, speaking one would want the WAF (or IPS) for that matter not to be configured as a single point of failure (SPOF). In the diagram shown above there are two sets of load balancers (ELB) and external and internal one to allow for multiple WAS instances in in separate Availability Zones. However, some solutions such as Fortinet’s FortiWeb provide load balancing capability do not need the external load balancer.
For SaaS and online businesses looking for a simple solution to get started, AWS WAF is something to consider. AWS recently launched a Web Application Firewall as an add-on service to AWS CloudFront. AWS WAF detects and blocks malicious web requests targeted at web applications through rules that can help protect against common web exploits like SQL injection and cross-site scripting. Key concepts associated with AWS WAF include conditions, rules, web ACLs, and actions which are explained in greater detail.
Conditions inspect incoming requests. The WAF looks at the request URI, the query string, a specific HTTP header, or the HTTP method (GET, PUT, and so forth). Because attackers often attempt to camouflage their requests, conditions can also include transformations that are performed on the request before the content is inspected. Conditions can also look at the incoming IP address, and can match a /8, /16, or /24 range. They can also use a /32 to match a single IP address.
Rules reference one or more conditions, all of which must be satisfied in order to make the rule active. For example, one rule could reference an IP-based rule and a request-based rule in order to block access to certain content. Each rule also generates Amazon CloudWatch metrics for tracking and monitoring.
Actions are part of rules, and denote the action to be taken when a request matches all of the conditions in a rule. An action can allow a request to go through, block it, or simply count the number of times that the rule matches (this is good for evaluating potential new rules before using a more decisive action).
Web ACLs (Access Control Lists) reference one or more rules, along with an action for each rule. Each incoming request for a distribution is evaluated against successive rules until a request matches all of the conditions in the rule, then the action associated with the rule is taken. If no rule matches, then the default action (block or allow the request) is taken.
Intrusion Detection System (IDS) – An intrusion detection system (IDS) is an appliance or capability that continuously monitors the environment and sends alerts when it detects malicious activity or policy violations and produces reports for analysis. IDS come in a variety of flavors and vary in their level of sophistication and cost. For most organizations hosted in cloud platforms such as AWS there are many choices for implementing IDS capabilities using technologies such as Splunk or Elasticsearch amongst others. An IDS system ensures the continuous monitoring of the environment at the network level as well as resource level from a configuration management perspective. Cloud platforms such AWS provide this capability through services such as VPC Flow Logs, Cloudtrail and Cloudwatch metrics. By adding a simple logging and dashboarding capability the cloud operations team can detect issues in the environment. The screenshot below provides an overview of the metrics and monitors associated with the VPC Flow service to analyze network traffic across the VPC. Key metrics such as Rejected Packets based on the flow rules setup in the environment. Diagram below shows a Kibana dashboard.
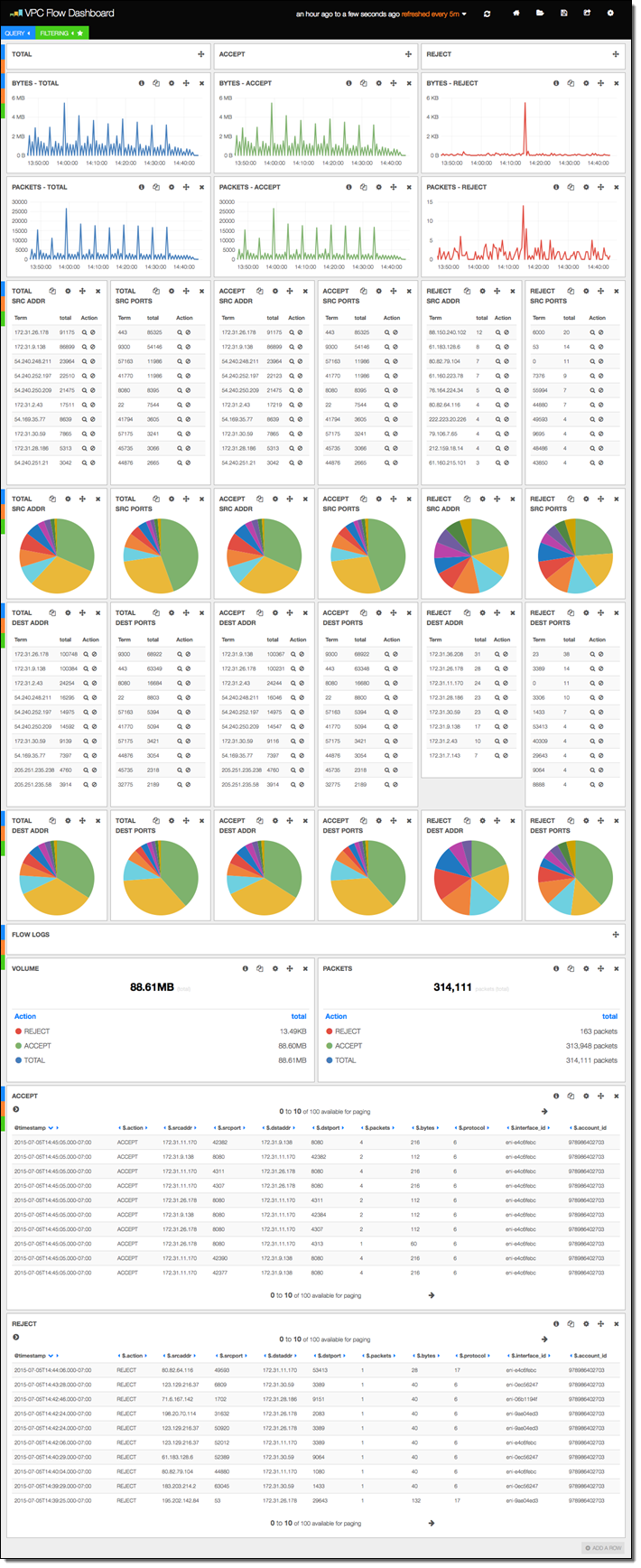
Figure 2: Diagram showing a IDS Dashboard using Kibana and Elasticsearch for AWS VPCFlow Logs
IDS systems come in various shapes, flavors and price points. Depending on the nature of the business, compliance requirements, threat level and sensitivity of the data, one most select and configure the most appropriate solution.
Please contact us for a free consultation and assessment of your cloud hosting environment or send us an email at solutions@stackarmor.com if you have any questions on AWS security architecture, vulnerability management and compliance requirements.


