
As DoD agencies continue their migration of sensitive workloads to the cloud, there is a greater need to ensure those workloads are deployed around the rigorous DoD Cloud Computing Security Requirements Guide (SRG) at Impact Levels 4 and 5. Systems categorized at Impact Level 5 (IL5) are allowed to host non-public, unclassified National Security System (NSS) system data (i.e., U-NSI) or non-public, unclassified data. The work to support the path to IL5 is made easier by both stackArmor’s proprietary ThreatAlert® Authority To Operate (ATO) Accelerator and the company’s experience supporting the technical and architectural implementation of IL5 controls. ThreatAlert® ATO Accelerator provides a proven, independently audited secure digital platform that includes (1) a landing zone, (2) an “in-boundary” cloud general support system (GSS) and (3) compliance controls for the DOD IL5 package/SSP (System Security Plan).
stackArmor provides our clients a suite of implemented security controls, evidentiary support and artifacts, and necessary continuous monitoring reports that support the successful completion of a system’s authorization & assessment phase. This pre-packaged solution results in a significant reduction of the time and effort associated with delivering a compliant FedRAMP High IL5 system and in achieving its ATO.
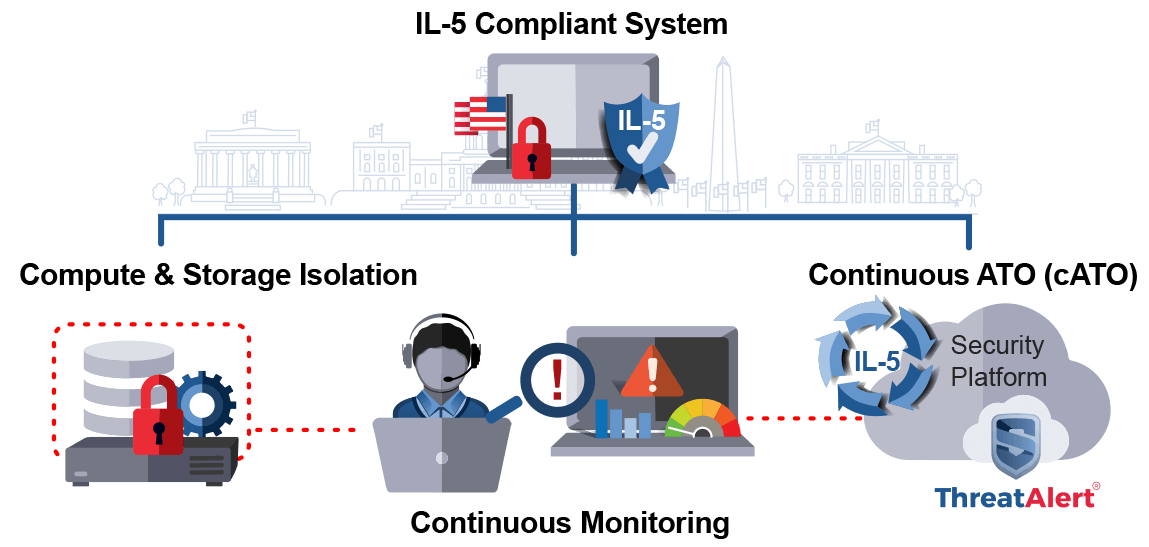
IL-5 and Data Isolation Requirements
When stackArmor is called upon to implement a FedRAMP+ DoD IL5 environment for DoD customers, we prioritize two key primary technical requirements required by the IL5 scope – compute and storage isolation. These isolation requirements, identified in Section 5 (Security Requirements) of the Cloud Computing SRG, are met using the tested and hardened stackArmor architecture, built on the AWS GovCloud infrastructure.
stackArmor further ensures the security and compliance of our customers IL5 environments by supporting the system with personnel that are US citizens and have completed full background checks.
In addition, all virtual instances within the IL5 environment are configured as ‘dedicated instances’, ensuring that the hosts and the storage running on the hosts operate within a physically and virtually segmented operating environment, isolating the data from any other tenants within the CSP data center.
Continuous Monitoring and IL5
stackArmor provides continuous monitoring (ConMon) and managed services for customer DoD IL5 environments through complex system alerts, customer-facing dashboards, and the performance of both scheduled and unscheduled monitoring activities. These activities include, but are not limited to; weekly audit log correlation analysis, daily technical working sessions, bi-weekly security and compliance review meetings, and weekly vulnerability scanning on all components of the platform. The technical working sessions are collaborative meetings that allow the client the opportunity to discuss details around application and platform engineering activities. The security and compliance meetings are conducted in close coordination with our client’s cybersecurity department. Vulnerabilities discovered during the ConMon process are documented as service tickets. Those tickets are assigned resources and priorities to ensure they are mitigated within the requisite timeframes of IL5. Cybersecurity and operational alerting is configured within the environment to automate critical severity alerts which have pre-defined workflows and playbooks to ensure a rapid and effective response for our clients.
ThreatAlert® Security Platform Supporting IL5
A key component that drives operational efficiencies and provides a single pane of glass view into our clients’ security and compliance is stackArmor’s ThreatAlert® Security Platform. ThreatAlert® provides a unified security platform for meeting the complex security and compliance FedRAMP+ DOD IL5 requirements. The fully managed platform is deployed “in-boundary” and offers ready access to critical security services for boundary protection, access controls, continuous monitoring such as security information and event management (SIEM), host-based security system (HBSS), incident response, reporting, vulnerability scanning and web application scanning. stackArmor’s continuous monitoring and security operations team uses these is tool on a daily basis to support its clients’ DoD IL5 environments. The platform supports the implementation of a true continuous ATO (cATO) capability including using a hardened CI/CD pipeline with integration for automated execution of critical compliance activities.




