stackArmor provides post migration support and management services for organizations adopting cloud services. stackArmor’s Managed Services are based on our Well-Managed Cloud Framework. Our framework is based on over 10 years of cloud operations experience and draws on Amazon’s Well Architected Framework, Microsoft’s Cloud Operating Model, Google’s Site Reliability Engineering (SRE), ITIL and NIST publications. The stackArmor Well-Managed Cloud framework provides a cloud operators point of view and incorporates best practices based on real operational experience.
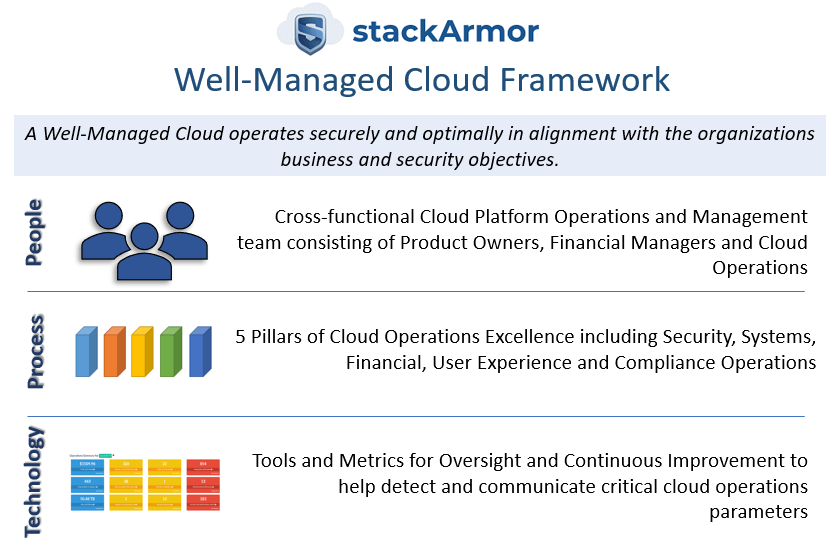
Our services portfolio includes managed services, managed security services and compliance services for regulated markets in compliance with FedRAMP, FISMA and CMMC requirements. Specific services include:
– Patching and vulnerability scanning using cloud-native as well as best of breed SCAP compliant tools for Linux and Windows workloads.
– Backup and service restoration for highly available workloads.
– Continuous logging, monitoring, co-relation analysis, and alerting based on 24/7 SLA’s.
– Compliance reporting, POAM management and evidentiary support.
– Technical support for platform services and optionally for application and data services.
The stackArmor managed services and managed security services offering is fully managed by our integrated Security Operations Center (SOC) staffed with US-based AWS certified SecDevOps Engineers delivering incident response, compliance reporting and remediation assistance.

Active Threat Hunting and Incident Response Services
Effective cybersecurity means going beyond passive logging, monitoring and alerting and requires active threat hunting, incident response and remediation. Our integrated security and compliance platform architecture covers the full-stack including Cloud, Containers, Data and Applications. We also provide integrated compliance reporting for NIST SP 800-171, NIST SP 800-53, HIPAA and GDPR compliance. End to end solution that includes Security Operations, Analytics, Response and Remediation delivered as a service for regulated markets with strong compliance requirements. The service includes dedicated SecDevOps Engineers and Analysts constantly monitoring and generating customized alerts, reports and remediation recommendations. stackArmor ThreatAlertTM is the only proven SOAPA and SOAR solution for regulated markets in public sector, higher education and healthcare markets.

Cost-Effective Security and Compliance Solution
stackArmor provides an end-to-end security and compliance service that helps organizations avoid having to hire expensive and scarce cybersecurity and cloud security experts. Our flexible consumption based cost model allows organizations to get best in breed security services at a highly affordable price. We provide a full set of SecDevOps engineers and analysts who are certified and experienced in AWS engineering and operations support using AWS recommended security best practices contained in the Well-Architected Framework (WAF). We partner with our customers to provide a cost-effective and customized solution that addresses urgent and critical needs that supplement and support our customers’ security and compliance needs.

Full-stack Cloud Security and Compliance Service
Comprehensive security coverage including vulnerability management and penetration scanning of AWS cloud configurations, Docker containers, Cloud instances, Applications and Data integrity checks, malware and anti-virus scans delivered in a single solution. Our continuous monitoring report provides coverage on major and critical security performance indicators. We meet the compliance standards for all major security standards including PCI-DSS, HIPAA, FFIEC, ISO 27001, FedRAMP, NIST 800-171 and FISMA.
Monitoring Coverage and SLA’s
stackArmor Managed Security Services covers the full-stack and has been developed based on NIST, DOD DISA, OWASP, FedRAMP and other Industry best practices and standards. The table below provides an overview of the threats and vulnerabilities included in the service:
| Service Scope | Description | Frequency of Check/Scan |
| Cloud Configurations | This scan includes common misconfiguration and security best practices that are recommended for protecting data and access including VNET/VPC, Identity/IAM, Blob/S3, RDS and other cloud services. | Daily scan |
| Operating System | Scans and reports operating system and application server vulnerabilities based on NIST CVE scores. | Recommended at least monthly but could be more frequent |
| Docker Containers | Deep scan of container image for common vulnerabilities based on NIST CVE scoring. | Recommended as part of the CI/CD pipeline |
| Operational Threats | Aggregated collection of findings from common cloud services such as AWS CloudTrail, CloudWatch, and GuardDuty for Account, Instance scanning and unauthorized access. | Continuous Scan |
| Data Files | Advanced intrusion detection to detect file integrity issues and report system intrusions. | Daily |
| Anti-Virus and Malware Scanning | Integrated antivirus engine for detecting trojans, viruses, malware & other malicious threats. | Daily |
| Custom Scans and Inputs | Specialized scanners and integrations with industry leading security solutions including Palo Alto Network, Splunk and Trend Micro amongst others. | Dependent on requirements |
The service is constantly being enhanced and augmented to cover new types of threats and vulnerabilities to provide highly responsive and updated security coverage.
The service delivery model includes one-time cybersecurity architecture reviews, vulnerability and penetration scans or continuous monitoring based on customizable reporting requirements. The service delivery includes incident response with customizable alerts, reports and remediation consulting. The stackArmor Cybersecurity Platform can be deployed as a dedicated service within the boundary of the customers’ environment or delivered as a shared service to meet various business, technical and security needs.
The pricing model is flexible and is based on the size of the environment and required SLA’s.