Crushing the 10 Tenets of DoD CSRMC — The Future is ThreatAlert®
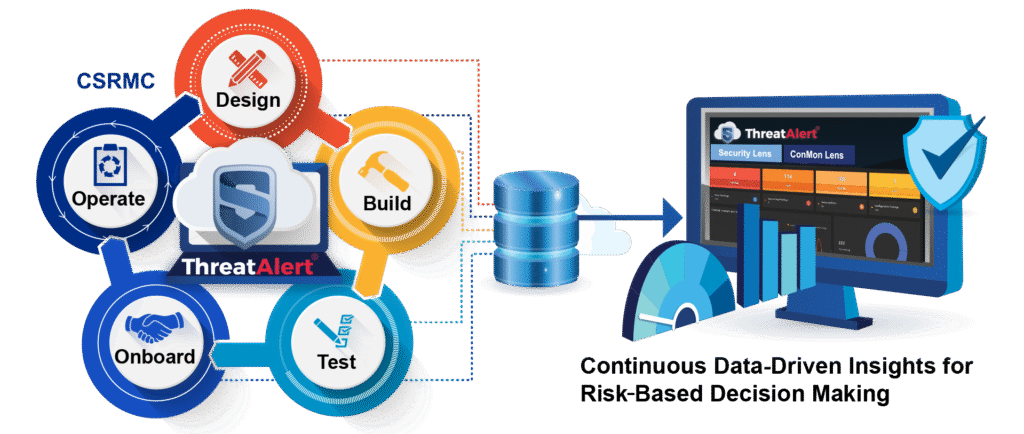
If the Risk Management Framework (RMF) was the long-running compliance opera: grandiose sets, endless rehearsals, dead-eyed troop members that just want it to end; the Cybersecurity Risk Management Construct (CSRMC) is the punk-rock reboot with a break-stuff attitude, razor-sharp set list, and the Hell’s Angels doing crowd control. The Department of Defense (or should I say, Department of War? No, seriously, I’m asking…) formally unveiled the CSRMC in late September 2025, positioning it as the successor to the legacy RMF and centering it on a five-phase lifecycle (Design → Build → Test → Onboard → Operate).
CSRMC | Cybersecurity Risk Management Construct

Why the switch? A decade of RMF inside DoD taught everyone the same lesson: static artifacts age like dead beef in a hot car during a Phoenix summer. CSRMC replaces the long-since zombified RMF with something that resembles a living thing capable of breathing fresh air. It’s chock-full of talk about continuous signals, automation, and operational accountability. It explicitly aims to be faster, less burdensome, and more accurate for people who need to make real-life, risk-based decisions. It’s risk management goodness.
The new CSRMC was being socialized across the community within days of the announcement. Early industry readouts say the quiet part out loud: CSRMC represents a break from RMF’s inescapable paperwork gravity to a universe favoring query-driven validation and continuous assessment. It means risk management moves at mission speed. At stackArmor, that’s a language we speak fluently. Our ThreatAlert accelerator, years ahead of its time, was purpose-built for this era. Dashboards are executable, evidence is machine-readable, and ATO is a living state rather than a calendar event.
If you’ve ever watched an ATO morph into a months-long scavenger hunt for screenshots, you know the feeling. This isn’t cybersecurity, it’s cosplay with clipboards. We’ve said it before, and we’ll say it louder for the folks in the back: screenshots are for chumps. We built ThreatAlert to end the theater and operationalize security, the way the DoD’s new CSRMC actually intends.
The CSRMC boils down to ten strategic tenets. Keep reading to see how ThreatAlert doesn’t just “meet” the tenets, but crushes them.

Automation
Our Orchestration & Automation Module (OAM) runs the playbook, so humans don’t have to: scheduled ConMon tasks (CTS), policy-as-code alerting, and auto-population of POA&Ms. Findings flow through the Intake Processing Module (IPM), are normalized in a common schema, and get worked to closure via the Finding Lifecycle Manager (FLM). That’s not “workflow,” that’s throttle-open orchestration.

Critical Controls
Security Lens centralizes high-signal findings and ties them directly to tickets and owners. ConMon Lens maps those same “critical” items to NIST 800-53 obligations so leadership sees both the vulnerability and the control impact in one pane. Translation: attention goes to exploitable gaps, not vanity metrics.

Continuous Monitoring & ATO
ThreatAlert’s query-based compliance and dashboarding show running state, not last quarter’s PDF, and backs every chart with machine-readable evidence. Our Serverless Relay (TSR) pushes alerts to Slack/Git workflows the instant conditions change, while ConMon tasks continuously generate the artifacts assessors actually use. That’s living, breathing ATO, not calendar-based theatrics.

DevSecOps
Our ThreatAlert Container Scanner (TCS) can be dropped into CI/CD and blocks risky images at the gate (Trivy in the loop). Our infrastructure-as-code (IaC) locks the system state like clockwork. Every change follows Git-backed change control. Every finding becomes a Git issue with evidence attached. Every merge enforces security policy like a well-paid bouncer. Shift left becomes ship right.

Cyber Survivability
We harden the platform and the workflows. Vulnerabilities are continuously scanned, hosts are instrumented (HIDS/HIPS), and detection => triage => fix is a single system of record. With automated dashboards and watch-officer-ready feeds, high-risk conditions get escalated fast, up to and including disconnect decisions. That’s what survivability looks like operationalized.

Training
ThreatAlert doesn’t just surface findings—it teaches by making compliance intent obvious. Security Lens tells engineers what broke; ConMon Lens shows why it matters; FLM embeds expected remediation steps. Over time, your organization learns to reason in controls as code, not binders as lore. (Your interns will thank you.)

Enterprise Services & Inheritance
ATOM (our ATO Machine) stands up secure landing zones that bake in enterprise controls: IAM, logging, NGFW, scanning, ticketing, from day one. Tenants inherit zero-trust guardrails instead of re-inventing them. The Automated Documentation Module (ADM) creates a hierarchy of reusable Component Definitions that can be assembled like children’s blocks to create your authorization package. That’s what secure-by-default actually means.
Operationalization
Everything is executable: queries, tasks, dashboards, and even evidence generation. Our engineer-designed Telemetry and Orchestration layer creates a data lake that pulls data from SIEMs, scanners, cloud APIs, virtually any running service, and normalizes the schema so dashboards are always current. Risk isn’t narrated, it’s computed, routed, and owned.

Reciprocity
This is the nearest and dearest tenet to stackArmor’s heart. Because our evidence is machine-readable and tied to authoritative APIs, reciprocity ceases to be a magical wish and becomes the way. Need to show another AO the same control proof? We don’t export a scrapbook; we re-run the query and hand over structured results. Clipboards are dead; in query-we trust – Come and See.

Cybersecurity Assessments
ThreatAlert’s FLM treats assessments as first-class citizens: ingestion, deduplication, severity mapping, and automated tasking are built-in. Dashboards give assessors drill-downs, not off-topic, mindless data dumps. When the construct calls for threat-informed, continuous validation, our answer is simply: Boom! Done! What else ya got?
The Lifecycle Fit
(Design → Build → Test → Onboard → Operate)
CSRMC reframes risk around a five-phase lifecycle and expects telemetry to feed ISCM throughout. ThreatAlert was literally designed for that loop: instrument early, automate often, and keep the system lifecycle fed with live data. The result is a repeatable playbook with automated dashboards, alerts, and data based on the actual running system state. For all the decision makers in the world, imagine making a decision with data that actually gives you an understanding of system risk. What a concept!
Why this works
And why the binder era never did and should be taken out to pasture…
Legacy compliance was never anything more than annual theater, point-in-time snapshots, error-prone artifacts, and false confidence. It didn’t manage risk; it was the source of it. It’s time it gets Old-Yeller’d!
Let’s forget about the RMF and step into the future. ThreatAlert aligns with CSRMC’s north star by replacing prose with proofs. Queries hit the actual running state; dashboards read from normalized inputs; and workflow engines turn ought into done. The bigger picture becomes:
- Paperwork transforms to data.
- Annual meaningless fire drills become meaningful, continuous checks.
- Trust-but-verify evolves into trust-because-we-verify.
And because ThreatAlert was designed by engineers to be fully capable and compliant from the start, we don’t simply bolt controls on later; we inherit and enforce them from the first commit, with segmentation, strong identity, encrypted traffic, and automated monitoring tuned for the mission. That’s survivability with receipts.
Copyright © 2025 stackArmor, Inc., a Tyto Athene Company. All rights reserved. All other trademarks not owned by stackArmor are the property of their respective owners, who may or may not be affiliated with, connected to, or sponsored by stackArmor. This document does not provide you with any legal rights to any intellectual property in any stackArmor product or solution.
About the Author:

Johann Dettweiler is the Chief Information Security Officer at stackArmor, a Tyto Athene Company. He is a seasoned cybersecurity leader with deep expertise in FedRAMP, NIST Risk Management Framework (RMF), and Governance, Risk, and Compliance (GRC) practices. With a career spanning over 19 years in the security and compliance space, Johann has held key roles as a Lead 3PAO assessor, chief advisor, and operational leader, bringing a comprehensive understanding of both technical and organizational risk management.
As CISO, Johann leads stackArmors enterprise security strategy, driving risk-based decision-making and guiding the organization in developing secure and resilient solutions. He plays a critical role in informing executive leadership on risk posture, ensuring that cybersecurity is integrated into every aspect of strategic planning and service delivery. Johann is the internal and external face of security for stackArmor, providing trusted guidance to customers navigating complex compliance landscapes




