Updated on 5/24/2025 with new developments in the area of ATO/RMF streamlining and acceleration.
As agencies modernize and increasingly move critical business processes and data online especially using cloud computing services, Federal agencies and their contractors, must undergo and maintain an Assessment and Authorization (A&A) process to obtain an Authority To Operate (ATO).
The traditional approach to A&A relies on manual, burdensome, and resource-intensive processes ill-suited to the dynamic nature of modern IT systems. Current challenges with ATOs include:
- lengthy ATO timelines and associated high costs
- lack of access to timely insights and vulnerability risk data
- high administrative burden
This blog post explores best practices designed to help reduce the time and cost of ATOs while improving access to risk data using process automation. The concept of Continuous ATO (cATO) is often discussed as a solution to this problem. But what exactly is cATO? How is it different from Continuous Monitoring? How does cATO fit within NIST RMF?
Let us understand these terms and how they all fit together. We will also discuss the importance of establishing a cATO Center of Excellence (COE), adopting a robust cATO platform, and implementing streamlined processes for continuous compliance. We will also provide a roadmap for organizations looking to embark on the cATO journey and explore the future of cybersecurity compliance in an increasingly complex and dynamic threat landscape.
NOTE: Initiatives like FedRAMP20X and DOD SWFT are recent attempts to reduce the time and cost of ATOs enabling faster access to commercial software, artificial intelligence and cloud technologies. The approach described below aligns with emerging practices and requirements.
What is Continuous ATO (cATO)?
Continuous ATO (cATO) is a modern approach to streamline the A&A process for information systems in the Federal Government. It leverages automation, standardization, and continuous monitoring (ConMon) to maintain a system’s Authority to Operate (ATO) more efficiently and cost-effectively than traditional methods. cATO is rooted in the NIST practices defined for Ongoing Authorizations. NIST defines Ongoing Authorizations as – maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions. It is important to note that “continuous” or “ongoing”
mean that security controls and organizational risks are assessed and analyzed at a frequency sufficient to support risk-based security decisions to adequately protect organization information. The key takeaway is that the organization defines the frequency of what continuous means in the context of its risk profile. Continuous could mean daily, weekly, or monthly even annually. The infographic below provides an overview of the overall process and relevant NIST controls.
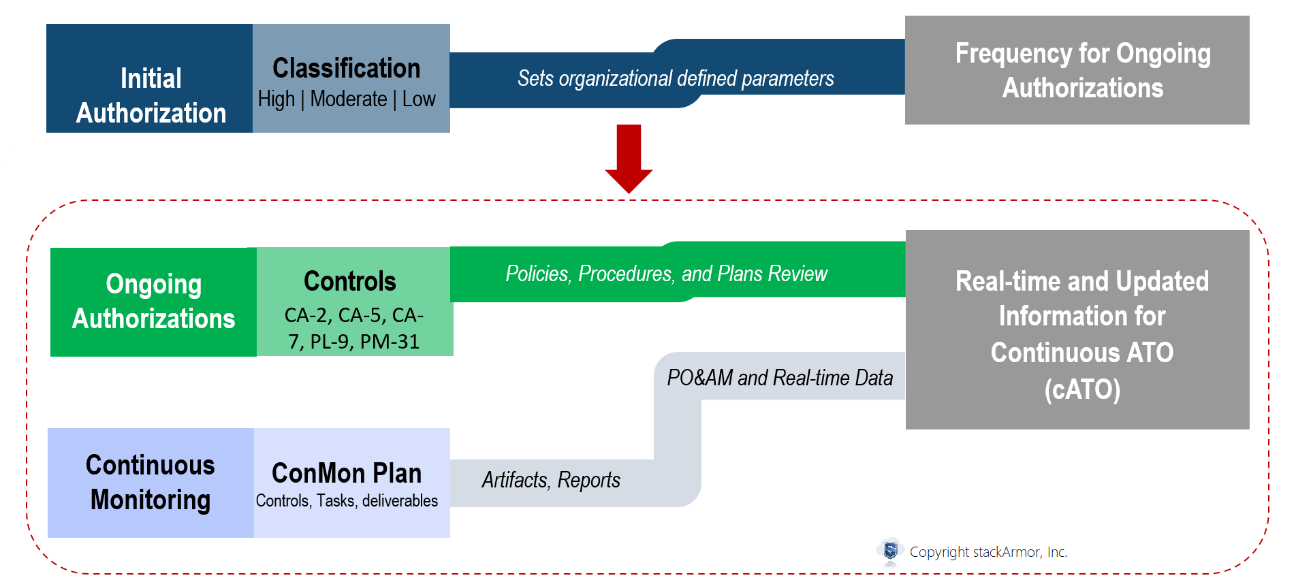
Figure: Initial Authorization and cATO Framework in the Context of NIST RMF
cATO shifts the focus from a point-in-time compliance exercise to a continuous, real-time assessment of a system’s security posture, aligning with the NIST Risk Management Framework (RMF) and FedRAMP program. As the infographic above demonstrates, cATO does not change the need to ensure compliance with existing requirements like continuous monitoring and managing changes using system change requests (SCR). Traditional A&A and Continuous Monitoring approaches often result in a snapshot view of a system’s security posture, which quickly become outdated in the face of rapidly evolving threats and the agility of cybersecurity adversaries.
cATO incorporates modern code-oriented principles such as security pipelines, use of APIs, generating machine-readable documents, and digital workflows into the A&A and ConMon processes. Adopting cATO as a transformation philosophy addresses the limitations of the traditional ATO process, by making the security operations and information assurance a first-class citizen in the digital transformation discussion. cATO emphasizes ongoing, real-time monitoring and assessment of a system’s security controls, allowing organizations to detect and respond to potential vulnerabilities and threats in a timely manner.
Takeaway:Â cATO transforms “Authority to Operate” into “Ability to Respond”.Â
Why do cATO?
cATO addresses the digital modernization challenges faced by CISOs and Information Assurance (IA) teams overburdened with meeting the increasing velocity of mandates and cyberthreats. Providing security and compliance teams with modern code-based tools and digital processes is the only way to reduce the compliance burden while meeting increasing mission security requirements and complexities.
|
Agency Challenges and Requirements |
Approach or Solution |
Transformation Catalyst |
|
Lengthy ATO timelines and associated high costs |
Introduce ato-as-code to modernize the A&A process with security pipelines, use of APIs, generating machine-readable documents, and digital workflows to produce artifacts automatically. |
Adopt ato-as-code approach by compliance team |
|
Overburdened Cyber Resources |
Streamline and automate vulnerability and asset data collection and integrate with digital workflows for generating artifacts like PO&AM, Inventory Repository and Risk Data. |
APIs, AI-triggered Workflows mapped to Controls |
|
Improving Real time risk posture assessment |
Dynamic cybersecurity threats require using zero-trust architecture principles, supply chain risk management and threat modeling to augment traditional CVE based vulnerability management. |
Security pipelines with automation and triggered process checkpoints. |
All the key facets of cATO – automation, standardization, and AI – come into play here. Since all teams work with the same set of documents and standards, all of which are kept up to date in real time, misunderstandings are minimized, enhancing collaboration.
Takeaway:Â cATO leverages automation, standardization and artificial intelligence to address the biggest pain points in the traditional A&A process.
How to adopt cATO?
Implementing cATO requires a comprehensive approach that encompasses people, processes, and technology. This approach includes the establishment of a dedicated cATO Center of Excellence (COE), the adoption of a robust cATO platform, and the implementation of streamlined digital processes.
1. Establish a cATO Center of Excellence (COE)
The cATO COE serves as a centralized hub for expertise, best practices, and resources related to continuous compliance. It brings together a diverse team of professionals, including cloud experts, security engineers, and compliance subject matter experts, who work together as an integrated product team (IPT) to drive the cATO transformation.
The COE is responsible for developing and maintaining a standardized security architecture that serves as the foundation for cATO. This architecture typically includes secure landing zones, strong boundary definitions, and a well-defined controls matrix that maps to the relevant security frameworks, such as NIST SP 800-53 and FedRAMP. The COE also develops and maintains a shared responsibility model that clearly delineates the roles and responsibilities of the various stakeholders involved in the cATO process, ensuring that everyone understands their part in maintaining continuous compliance.
2. cATO Platform
A robust cATO platform is another critical component of a successful cATO implementation. Unlike traditional GRC, the provides a centralized, integrated environment for managing all aspects of continuous compliance, including secure landing zones, an OSCAL-ready package with pre-configured technical controls, procedures, and policies, as well as continuous monitoring and ongoing authorization capabilities. The cATO toolchain is seamlessly integrated with modern software operations & management tools like GitOps, DevSecOps and APIs. Â
3. Digital Processes & Workflows
A&A processes and Continuous Monitoring activities are decomposed into discrete actions and implemented as digital workflows. Streamlined cATO processes need to be designed using systems engineering principles that emphasize using “ato-as-code” approaches to remove or reduce the need for traditional MS-Word or MS-Excel based artifacts. Using machine readable artifacts codified in standards like OSCAL, the consistency and quality across systems, vendors and programs can dramatically reduce the administrative burden on cybersecurity teams. By allowing easier access to accurate and reliable risk data allows cybersecurity teams to focus their time on analyzing threats.
Takeaway:Â a robust approach to cATO has three main components:Â COE, platform, and processes.
How to Begin the cATO Journey
Embarking on the cATO journey involves careful planning and execution. Organizations should start by conducting an “as-is” analysis to assess their current state of compliance and identify gaps or challenges. Based on these findings, they can establish a cATO COE with key personnel, roles and responsibilities, and clear goals and objectives.
To demonstrate the value and feasibility of cATO, organizations should perform a pilot project focused on a single system or application. This pilot should include all the key components of cATO, such as a standardized architecture, automated testing and validation, and continuous monitoring and reporting. Once the pilot project has demonstrated success, organizations can expand the cATO approach to additional systems and applications in a phased approach.
Throughout the cATO journey, organizations should continuously monitor, measure, and optimize their processes, seeking opportunities to improve and streamline their efforts. This may include adopting new technologies, refining processes, or expanding the scope of the COE.
Takeaway: see where you are now; do a pilot; expand to production. Also, read about the ATO as Code project developed by the Cyber COI at ACT-IAC and sponsored by OPM.
Conclusion
cATO represents a significant shift in cybersecurity compliance, enabling organizations to maintain a continuous state of audit readiness while reducing the burden on product teams. By leveraging automation, standardization, and continuous monitoring, organizations can significantly reduce the time, cost, and effort required to achieve and maintain an ATO, while also improving the accuracy and consistency of their compliance documentation and enhancing transparency and collaboration between assessors and product teams.
To achieve the benefits of cATO, organizations must adopt a comprehensive approach that encompasses people, processes, and technology. This includes establishing a dedicated cATO COE, adopting a robust cATO platform, and implementing streamlined processes for continuous compliance. Organizations must also foster a culture of collaboration and continuous improvement and invest in the necessary resources and expertise to make cATO a success.
As the threat landscape continues to evolve and the complexity of IT systems grows, cATO will play an increasingly important role in cybersecurity compliance. By embracing this approach, organizations can not only achieve compliance but also improve their overall security posture and better serve the needs of their stakeholders. While the journey to cATO may not be easy, it is certainly easier than the status quo, and well worth the effort.
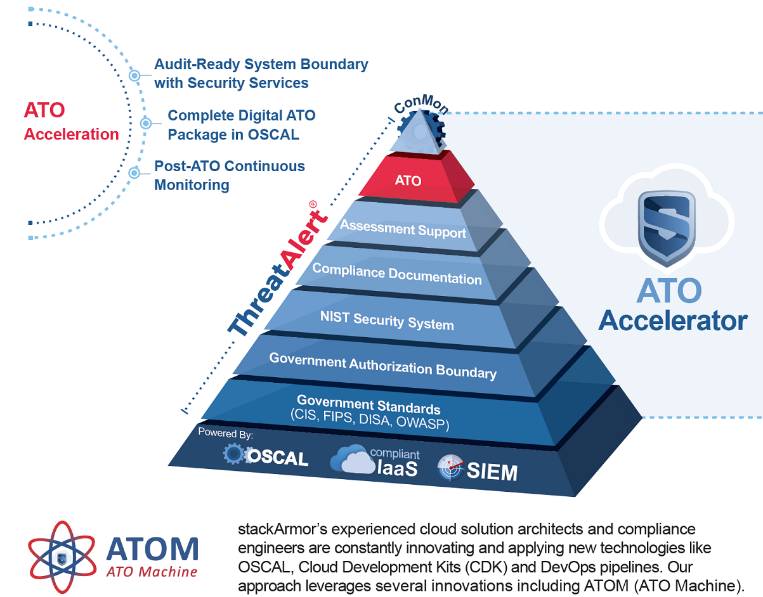
About stackArmor:
stackArmor ThreatAlert® is a cATO accelerator solution with a proven track record in helping organizations rapidly meet NIST SP 800-53 Rev 5 based ATO security requirements. Key elements of the solution include:
- Secure Landing Zone: Dedicated authorization boundary with separation for applications, users and data with a common Cloud General Support System (GSS).
- OSCAL Ready Package: Complete Rev 5 package with technical control. implementations, procedures, and policies.
- Ongoing Authorizations: On-going continuous monitoring in compliance with Agency, FedRAMP or DOD requirements.
- Experienced Experts: Former 3PAO’s and Government cloud, security and compliance experts with DevSecOps skills
The ThreatAlert® cATO Accelerator helps agencies save time and money by providing a pre-engineered, NIST SP 800-53 Revision 5 compliant cloud-hosting environment fully equipped with security services, compliance documentation and continuous monitoring services including security operations, incident response and compliance reporting with periodic tasks such as weekly log reviews, monthly PO&AM reporting and Vulnerability Management & Reporting. The ThreatAlert® cATO Accelerator is delivered “in-boundary” avoiding external connections. Schedule a briefing and learn more about you can begin your cATO transformation journey.




