Preparing for FedRAMP Certification and Authorization
FedRAMP is a government-wide program that promotes the adoption of secure cloud services across the federal government by providing a

40% reduction in ATO cost with included documentation package
Our unique ATO accelerator provides a “pre-fab” security stack that is accompanied by a complete set of documentation templates with audit-ready security control descriptions. We are the only ATO acceleration solution provider that transparently shares the controls matrix meeting more than 70% of the controls for FedRAMP, DOD CC SRG, and CMMC compliance. Want to know more about FedRAMP ATO costs? Read our blog.
FedRAMP is a government-wide program that promotes the adoption of secure cloud services across the federal government by providing a
The Cybersecurity Maturity Model Certification (CMMC) is a unified standard for implementing cybersecurity across the Defense Industrial Base (DIB), which includes over 300,000 companies in the supply chain.
Commercial organizations looking to sell cloud-based solutions to Federal agencies must comply with FedRAMP security requirements.
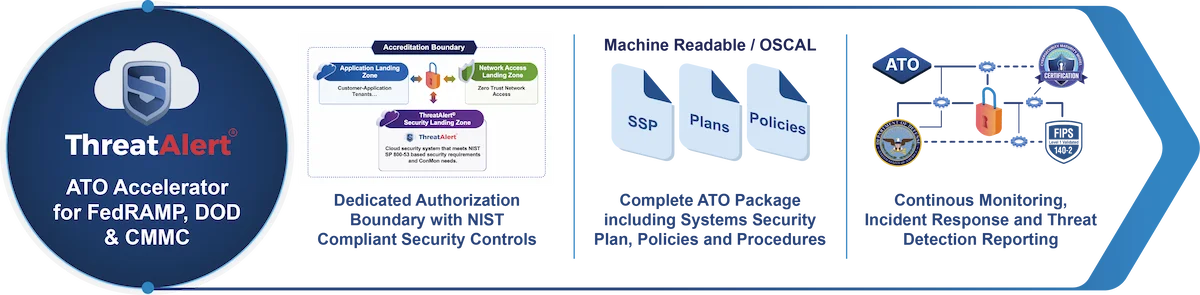
ThreatAlert® is uniquely designed to provide a comprehensive and tailored service that accommodates specific client requirements around tools, integrations, and hybrid team models. The ThreatAlert® ATO Accelerator is vetted by AWS to rapidly configure and deploy a dedicated authorization boundary, NIST compliant security services, and the complete ATO documentation package, including policies, procedure,s and plans. ThreatAlert® supports FedRAMP High, Moderate, Low; DOD CC SRG IL-2, IL-4, IL-5, and CMMC 2.0 Level 2 and Level 3 baselines, including CUI.
The service includes the entire range of FedRAMP advisory services and is priced as well as delivered in modular components that allow the customer to pick and choose specific components that best meet their needs. Further, we provide highly simplified and streamlined pricing based on micro, small, medium, or large environments that include virtual machines, containers, or serverless components. Schedule a free consultation and see if we can assist in your FedRAMP ATO acceleration efforts.