Large software vendors, global defense contractors and organizations operating in hyper regulated markets must meet very specific government cybersecurity requirements. These requirements include ensuring data sovereignty as well as compliance with specific standards like FedRAMP or ITSG-33 in the US and Canada respectively. The rapid emergence of data sovereignty requirements are driving the increased need for “in-region” deployments that provide the ability to contain the data within a pre-specified area. External connections to corporate services, other SaaS services, or other systems cause the assessors to take a real hard look at data flows. This scrutiny and extra due diligence can slow down the accreditation process. These unique constraints create challenges for large global organizations looking to meet complex regulatory requirements in a cost-effective manner.
This problem can be solved by using an “in-boundary” security and compliance model that limits the number of external connections and delivers a “region-gapped” service.
stackArmor’s cloud, compliance and security specialists pioneered the concept of “in-boundary” security and compliance deployments. There are multiple benefits to using an “in-boundary” deployment model:
- Faster audit as external connections are limited/few
- Flexibility in “upgrading” accreditation levels by removing “inheritance” dependencies
- Portability across geographical regions to meet sovereignty requirements
We launched the ThreatAlert® Security Platform in 2018 to deliver 18 plus security services directly mapped to NIST controls. The ThreatAlert® Security Platform is installed within the customers boundary ensuring that no data ever leaves the environment. This “in-boundary” deployment model uniquely accelerates ATO’s. We have successfully deployed the ThreatAlert® Security Platform to accelerate ATO’s at District of Columbia’s Health Benefits Exchange (DC-HBX), Department of Education, Department of Justice and numerous Cloud Service Providers (CSP) looking for FedRAMP accreditation.
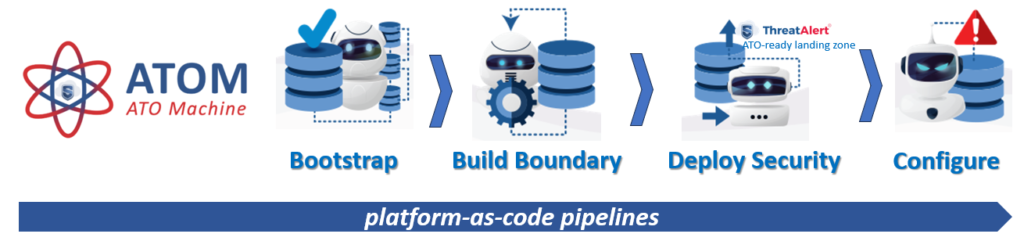
Today, we are excited to share our success in further accelerating the deployment of FedRAMP, FISMA/RMF, CMMC 2.0 and DOD compliant environments with the stackArmor ATO Machine (ATOM). stackArmor ATO Machine (ATOM) leverages platform-as-code to “shift-left” complex security service installation, configuration and operationalization tasks. stackArmor ATO Machine (ATOM) is the “deployment vehicle” for the ThreatAlert® Security Platform that stitches together discrete native and non-native services to deliver a highly operationally ready and auditable environment. The combination of stackArmor ATO Machine (ATOM) and ThreatAlert® Security Platform deliver a ready-made solution for organizations looking to deploy compliant platforms – faster!
What is Platform-As-Code (PaC)?
Platform-as-code (PaC) is a new paradigm for developing opinionated platforms that meet specific business and security requirements. PaC uses software development principles of modularity, abstraction, and maintainability. The result is greater rigor, consistency and standardization across the enterprise for deploying infrastructure and security services thereby saving time, money and avoiding costly mistakes.
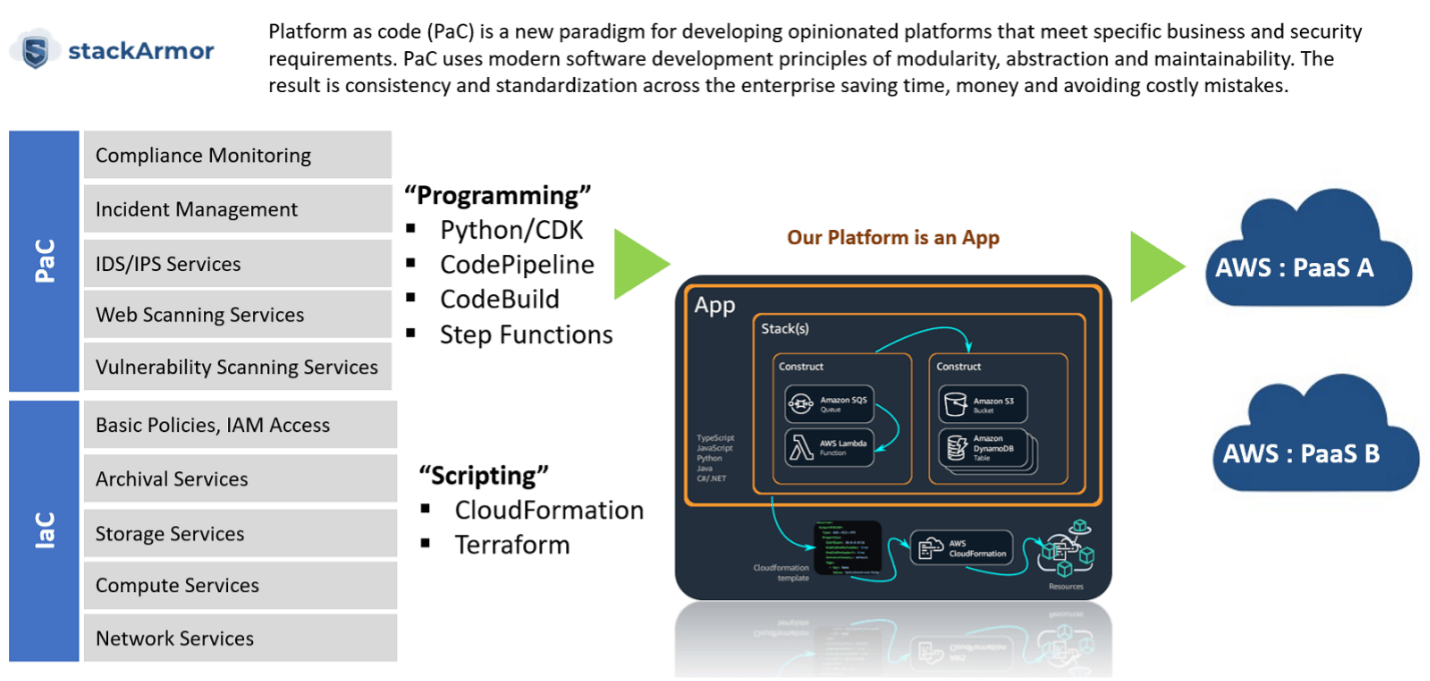
It is important to note that PaC is a mission use-case driven approach to deliver an auditable and compliant platform that includes infrastructure, security and continuous monitoring services. PaC builds on the foundational services enabled by infrastructure-as-code (IaC). In many ways, PaC starts where IaC stops, to further automate the installation, configuration and operationalization of higher order servicses required for compliant environments. With platform-as-code (PaC) we can build “apps”, which can then be readily deployed or instantiated to deliver PaaS. A large organization can construct many “apps” – one for FedRAMP, another for HIPAA and a third for Canada’s ITSG-33 as an example. Platform-as-code enables greater consistency, auditability and flexibility through well known software development practices like abstractions, encapsulation, inheritance, as well as a rigorous SDLC to ensure a solid product. A large part of this transition has been enabled by the arrival of automation services, standardized reference architectures and infrastructure as code pipelines.
Introducing stackArmor ATO Machine (ATOM)
stackArmor ATOM is a faster, consistent, repeatable way to deploy a secure by design cloud hosting boundary with strong security guardrails and embedded security services compliant with NIST standards. stackArmor’s ATOM delivers an opinionated secure landing zone populated with stackArmor’s ThreatAlert® Security Platform with secure configurations such as DISA STIGs, CISA ScUBA, or CIS benchmarks as appropriate. Leveraging coding constructs like Terraform, Cloudformation, Ansible and Python code with CDKs, our ATOM platform-as-code implementation accelerates the technical deployment of our “in-boundary” ThreatAlert® solution, reducing implementation time by up to 60%. By leveraging ATOM, global ISV’s and customers looking to offer accredited cloud services across hyperscale cloud regions can develop a standardized and compliant SaaS platform that can be easily deployed and maintained.
stackArmor ATOM provides DOD/DISA and NIST control driven services such as:
- SCAP compliant vulnerability scanning services
- OWASP web scanning services
- Anti-virus and malware protection
- Host-based IDS/IPS services
- Security incident and event management
- Incident response and management
- Continuous monitoring services for cATO
stackArmor ATOM builds upon IaC best practices such as centralized governance, guardrails through Service Control Policies (SCP), separation of operations & user data and a consistent compliance posture across tenants and workloads. stackArmor ATOM platform-as-code builds upon cloud native automation frameworks and services such as Compliant Framework for Federal and DOD Workloads. Key capabilities include:
- CI/CD pipelines to deploy and update infrastructure via GitOps with central, in-boundary code repository
- Account vending machine which is a service catalog project that creates, and provisions accounts in and invites them to the Organization in the specified OU at launch
- NIST compliant security services with ThreatAlert® Security Platform providing security, networking and management services mapped to NIST SP 800-53 security controls and engineered as an “in-boundary” General Support System (GSS)
- Full-stack centralized logging including native cloud services, application services, container services and data services as well as identify services
- Seamless integration with our in-boundary SIEM to perform continuous monitoring, log correlation, and incident alerting
- Ensuring FIPS 140-2/3 validated cryptography for data in motion as well as at rest
- FIPS 140-2/3 validated MFA and Zero-trust access management
- Backup and recovery to meet data retention and multi-region requirements
- Proper segmentation of workloads and separation of security, management and operational data
- DNSSEC for both public and private DNS resolution
- Centralized authentication and authorization to all security services
If you are a DOD/Federal Mission Owner, Global ISV or Defense contractor looking to accelerate your mission while complying with government requirements and maintaining data sovereignty, then connect with us to see how stackArmor ATOM and the ThreatAlert® Security Platform can reduce the time and cost of your project.
Authors:
Matt Venne, Sr. Director of Solutions Architecture, stackArmor.
Ed Bender, Sr. Solutions Architect, stackArmor.