The Armory™: Accelerating FedRAMP ATOs on Google
The Armory provides an accelerated path to FedRAMP ATOs on Google Cloud, by offering Hosted ATOs, Managed ATOs and Continuous Monitoring of Agency Workloads in a cost-effective manner.

The Armory is a purpose-built, General Support System (GSS) cloud service offering designed to empower ISVs and Enterprises to conquer complex regulatory requirements on Google Cloud (GCP). The Armory provides a FedRAMP compliant architecture, deployment services, documentation, and audit support, along with continuous monitoring. The all-inclusive service includes in-boundary tools for automation, configuration, and account management, all within a FedRAMP authorized Assured Workloads environment managed to FR20x, CMMC, ITAR, FedRAMP High, and DoD IL4/5 standards.
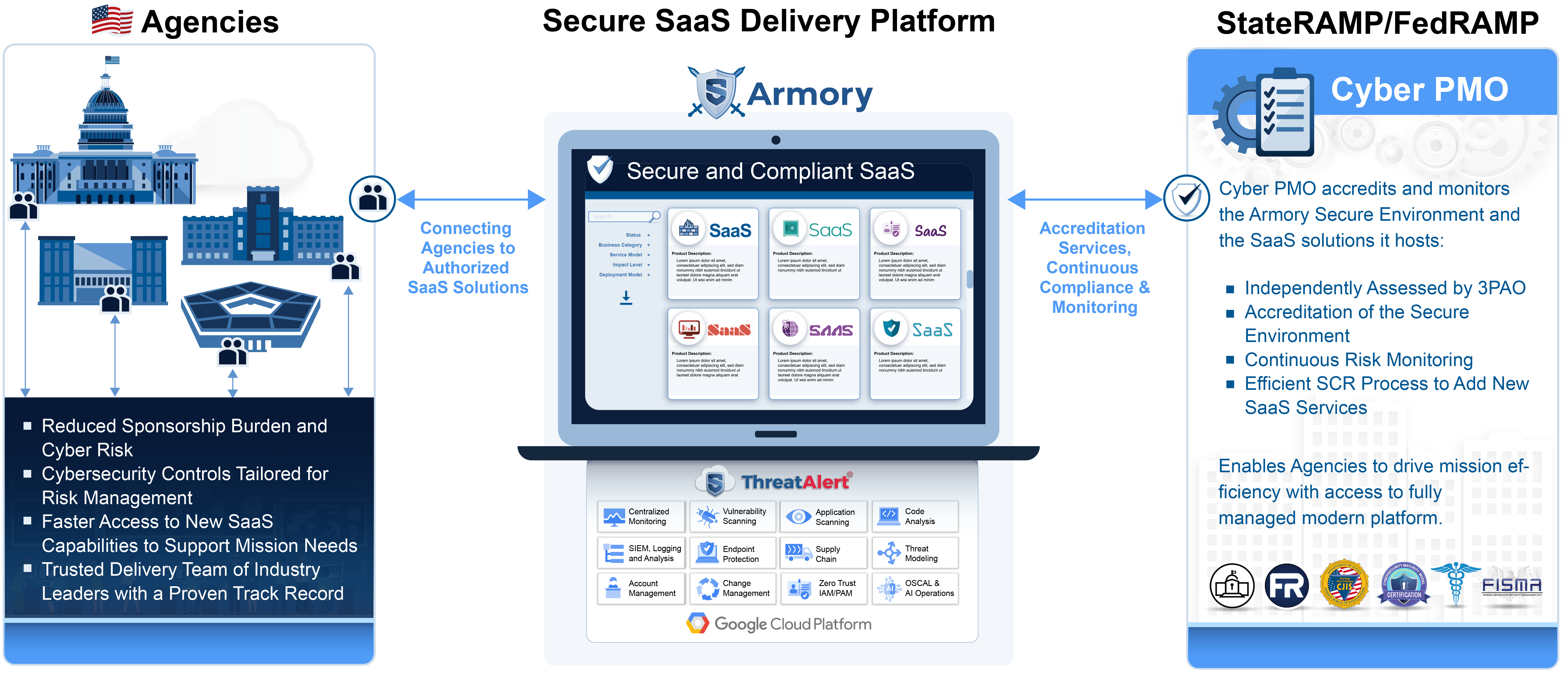
Armory provides a comprehensive Managed ATO solution for FedRAMP, offering a dedicated team of experts and a purpose-built platform to guide you through every step of the authorization process. From security control implementation to documentation and continuous monitoring, Armory ensures you meet FedRAMP requirements efficiently and effectively, minimizing risk and maximizing your chances of success.
The Armory accelerates FedRAMP ATO for Agencies and ISVs with a pre-authorized environment on Google Cloud. By inheriting pre-configured security controls and a streamlined compliance package, organizations reduce the complexity, time, and cost of achieving FedRAMP authorization, enabling faster, secure application deployments while meeting stringent government requirements.
For organizations seeking to maintain control over their infrastructure while meeting stringent compliance requirements, Armory offers Managed Assured Workloads for colocation. We provide the security controls, continuous monitoring, and expert guidance needed to achieve and maintain FedRAMP High authorization in your colocation facility
Armory20x hosted by stackArmor, provides a FR20x as a service accelerator for ISVs and AI companies looking to meet FR20x requirements. stackArmor’s compliance experts provide FR20x accreditation support, managed hosting, continuous monitoring and support using our Armory(TM) technology on the Google Cloud Platform.
Contact us to schedule a briefing.
Rally hosted by stackArmor, and distributed & supported by Carahsoft has been developed by Broadcom to provide enterprise agile management solutions to Government agencies. stackArmor’s leading cloud, security and compliance experts provide FedRAMP accreditation support, managed hosting, continuous monitoring and support using our Armory(TM) technology on the Google Cloud Platform.
Review FedRAMP Marketplace listing.
Clarity hosted by stackArmor, and distributed & supported by Carahsoft has been developed by Broadcom is a leading Strategic Portfolio Management (SPM) solution designed to give organizations confidence in their business decisions – especially as AI looms large. stackArmor’s leading cloud, security and compliance experts provide FedRAMP accreditation support, managed hosting, continuous monitoring and support using our ArmoryTM technology on the Google Cloud Platform.
Review FedRAMP Marketplace listing.
Qanapi is the first service available in the Armory and they are revolutionizing data security, compliance, and governance with its FIPS-validated API service, providing state-of-the-art encryption and protection at the data level. Designed to safeguard sensitive, industry-regulated, and mission-critical data, Qanapi’s API seamlessly integrates into any software, device, or network. Built on a zero-trust architecture, it ensures robust security across organizations of all sizes, in both the public and commercial sectors. With Qanapi, organizations can achieve the highest level of data protection and compliance, regardless of their environment.
Discover more at qanapi.com
Provided in conjunction with in-boundary security service deployments and FedRAMP Authorized GCP native services.
The Armory provides Continuous Monitoring (ConMon) for FedRAMP through the ongoing process of assessing, validating, and documenting security controls to maintain authorization and promptly address emerging threats.
Vulnerability scanning involves using automated tools to scan the Armory’s systems, networks, and applications for known vulnerabilities. These scans identify misconfigurations, outdated software, and other security weaknesses that could be exploited by malicious actors.
Armory simplifies compliance and auditability with comprehensive SIEM, logging, and analysis. Our platform ensures that all security-relevant events are captured, stored, and analyzed in accordance with industry best practices and regulatory requirements, providing a clear audit trail for compliance reporting
The Armory provides robust endpoint protection to safeguard sensitive data and maintain a secure cloud environment. These solutions include antivirus, anti-malware, host-based intrusion prevention systems (HIPS), and endpoint detection and response (EDR) capabilities.
The Armory implements stringent supply chain risk management (SCRM) requirements to ensure the security and integrity of all components and services used in the cloud system. This involves conducting thorough due diligence on all third-party vendors, assessing their security controls, and ensuring compliance with FedRAMP security standards.
Armory provides a proactive approach to Zero Trust security, continuously assessing risk and adapting security policies based on real-time conditions. Our platform helps you move beyond traditional perimeter-based security to a more dynamic and resilient model that protects your organization from modern threats.
Armory empowers proactive security with integrated threat modeling capabilities. Our platform helps you identify potential threats and vulnerabilities early in the development lifecycle, enabling you to design and implement more secure applications from the start.
The Armory ensures that access to the management and networking plane are properly controlled and secured. This includes implementing strong multi-factor authentication, authorization, and auditing measures for all user accounts, as well as regularly reviewing and managing account privileges to minimize the risk of unauthorized access.




