WAF or web application firewall helps protect your web applications from common web exploits such as SQL injection, Cross site scripting or XSS, HTTP flood attacks etc. These types of attacks can compromise security and data, affect availability of the web application or allow attackers to use resources without your knowledge and incur exorbitant amounts of usage bills. AWS WAF can be deployed on either Amazon CloudFront as part of your CDN solution, the Application Load Balancer (ALB) that fronts your web servers or origin servers running on EC2, or Amazon API Gateway for your APIs.
All components required for this available in a form of a CloudFormation template, from which users can select from a set of preconfigured rules for a web ACL (Access control list) according to their requirement. The CloudFormation can be deployed and customized as shown below:
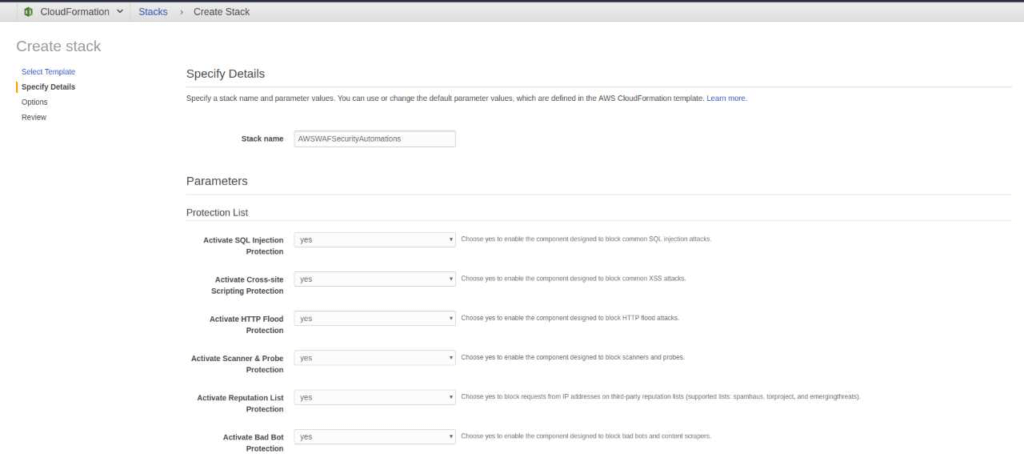
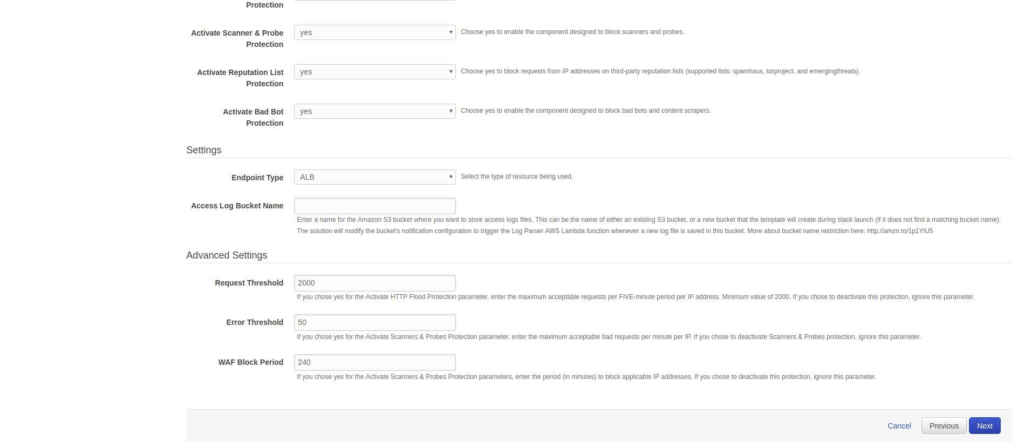
The CloudFormation deploys an architecture similar to the one shown below including an AWS WAF with rules, S3 bucket, AWS lambda etc.
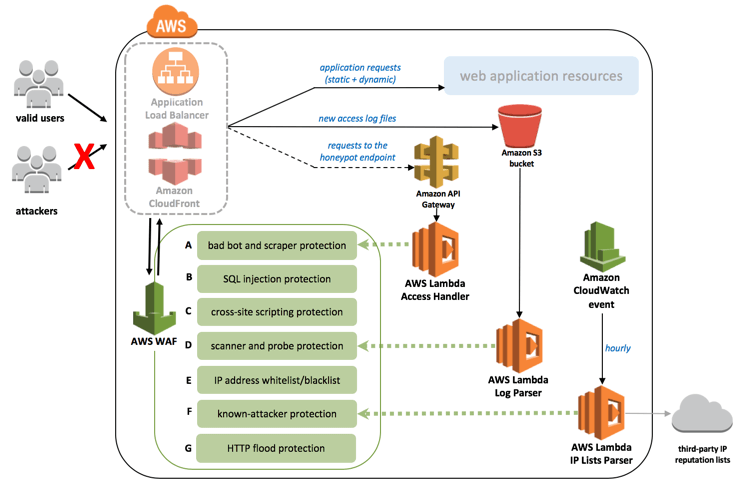
Image courtesy: Amazon Web Services (AWS)
This solution protects web applications against:
- SQL injection: Attackers use malicious SQL insert operations in web requests to try and extract sensitive data from your SQL databases. The solution blocks any potentially malicious web requests.
- Cross site scripting (XSS): In this type of attack, attackers use vulnerabilities in a benign website to inject malicious client-side scripts to a user’s browsers, which in turn compromises the infected user’s security.
- HTTP flood attacks: This mostly pertains to a class of attacks called Distributed denial of service or DDOS, where attackers send a unhand able number of packets to a web application to bring it down. The solution triggers a rate-based rule if a threshold of web requests is met.
- Scanners and probes: Scanners and probes act as the initial form of reconnaissance for attackers where they probe a web facing server and figure out the ports and tools/software on the server. In this solution, there is an AWS Lambda function that looks at the history of bad requests and blocks IP addresses from performing further scans.
- Known attacker origins: By using third party web reputation lists/ databases of known malicious IP attackers we can prevent them from accessing our resources. This solution automatically blocks requests from such entities.
- Bots and scrapers: content scrapers and bad bots are prevalent in the web and try to access your content in ways that are not indented. The solution blocks any such type of request.
The solution mentioned above can be integrated into your existing AWS ACL/WAF solution and can be modified to protect multiple types of web applications.
We hope this helped. Please let us know if you have any questions at solutions at stackArmor dot com.


