Developing a scalable and secure cloud architecture is a critical foundational block for a successful cloud transformation program. stackArmor has successfully developed and deployed platform-centric architectures based on DOD PlatformOne, Kubernetes and industry best practices that segment, segregate and encapsulate services based on their specific function. stackArmor’s architects have developed complex shared services platforms such as US Treasury’s Workplace.gov Community Cloud (WC2) on AWS, FDA’s Trusted Cloud Platform (TCP) and numerous commercial solutions for regulated markets. All stackArmor designs are documented and reviewed with clients to ensure that the designed solution performs to client expectations. stackArmor also offers a unique Design Assist and Review where stackArmor Cloud Solution Architects can help review and assist client teams looking to design their own solutions. All of our designs follow cloud solution architecture best practices including use of DOD Secure Cloud Computing Architecture (SCCA), DOD PlatformOne, and AWS Well Architected Framework (WAF). The diagram below shows a typical platform architecture developed by stackArmor engineers for organizations seeking to host multiple workloads while providing a common set of security and management services.
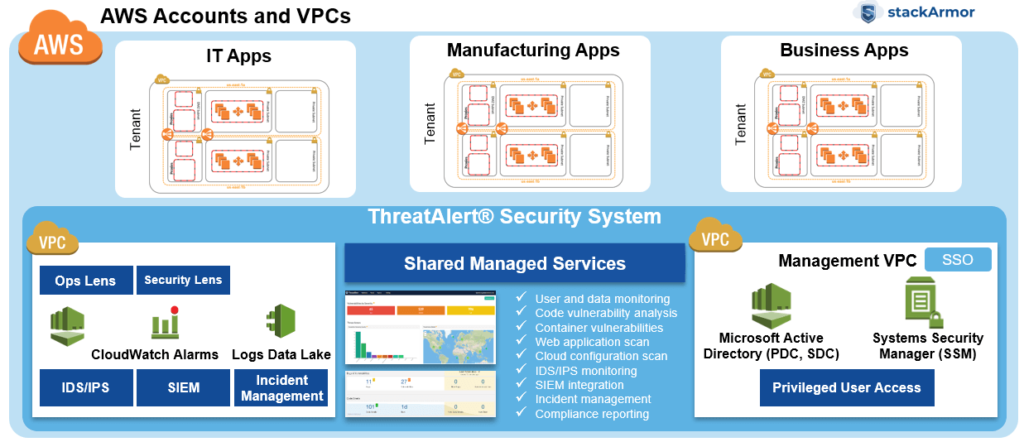
A well-architected cloud is one that is optimally and securely in alignment with business and security objectives of the organization. Our solution architecture and consulting services include:
Landing Zone Design
Defining and designing an optimal landing zone requires analyzing organizational requirements. For example we recently implemented a landing zone for a defense contractor handling sensitive data requiring a separate forensics enclave; a federal agency required a data containment zone for handling PII while another customer needed a IL-6 “solution template” landing zone limited to using IL-6 accredited services only. Landing zone design must take into consideration specific requirements.
Network Access and Connectivity
Setting enterprise networking connectivity using options like IPSec VPN tunnels, dedicated AWS DirectConnect or third-party solutions like AT&T NetBond or Zscaler. Extending the network boundary is a critical “on-ramp” to cloud that must deliver enough bandwidth, reliability and security.
User Authentication & Authorization
Understanding and designing the right user authentication, authorization and security services is critical for optimal user experience. There are a number of identity solution design considerations including federation, MFA, SSO and compliance requirements that drive the optimal architecture.
Containers, Serverless, Virtual Machines
The rapid evolution and adoption of serverless, kubernetes, docker and virtual machine based hosting options require the ability to design a solution that is future proof with the ability to support a heterogenous portfolio of systems.
Security Services
Analyzing and implementing the right types of security services is highly dependent on the confidentiality, integrity and availability requirements associated with the data. There are a number of standard services like patching, vulnerability scanning, logging, monitoring and alerting as well as more advanced services like threat hunting, forensics, and data loss prevention (DLP) amongst others.
stackArmor, Inc. a Tyto Athene Company, provides FedRAMP, FISMA/RMF, and CMMC/DFARS compliance acceleration services. stackArmor’s ThreatAlert® Security Platform reduces the time and cost of an ATO by 40%. We serve enterprise customers in Defense, Aerospace, Space, Government, and Healthcare markets as well as ISV’s looking to offer cloud solutions for Government.
Menu
© stackArmor. All Rights Reserved 2025.