By: Matthew Venne, Senior Solutions Director
In an increasingly interconnected world, securing digital assets and sensitive information has never been more critical. In a never-ending game of “cat and mouse, malicious actors and cyber security professionals go back and forth trying to one-up each other. As a result, the security required to protect digital assets has outgrown the “traditional” perimeter-based security model, where processes and identities are typically only authenticated once and then implicitly trusted. To adapt to the new network complexity, a new model, the “Zero Trust” security model, has gained prominence as a more robust and effective approach to safeguarding data and systems. Okta, a leading identity and access management (IAM) solution provider, has recently introduced its Identity Engine to implement Zero Trust principles. In this blog post, we will delve into how Okta’s Identity Engine implements Zero Trust and the benefits it offers for modern organizations.
Understanding Zero Trust
Zero Trust is a security model that assumes there is no implicit trust within or outside an organization’s network. Unlike the traditional “castle-and-moat” approach, where security is implemented mainly at the perimeter of the system, the core of Zero Trust can be boiled down to the old military adage: Never trust, Always verify. It emphasizes that organizations should scrutinize and authenticate every user and device trying to access their resources, regardless of their location.
Okta’s Identity Engine: The Foundation of Zero Trust
Okta’s Identity Engine is a comprehensive identity and access management platform that plays a crucial role in implementing Zero Trust. Here’s how it accomplishes this:
Enforcing Modern Authentication: Zero Trust starts with identity. Okta’s Identity Engine (OIE) ensures that only authenticated and authorized users gain access to resources. However, its not sufficient to just require strong passwords and multifactor authentication. Authentication is done using one or a combination of the 3 methods:
- Something you know – passwords, PINs.
- Something you have – a physical token (OTP or FIDO2) or digital certificate signed by a trusted CA.
- Something you are – biometrics (fingerprints, facial recognition, retina).
Passwords and PINs are becoming increasingly problematic for users – they are either too simple or too complex to remember. It’s better to rely on either possession-based factors or biometrics since those are not vulnerable to password cracking and password dumps from compromised systems. With Okta’s Identity Engine, you can craft global or application-specific policies to enforce the type of authentication you want to enforce.
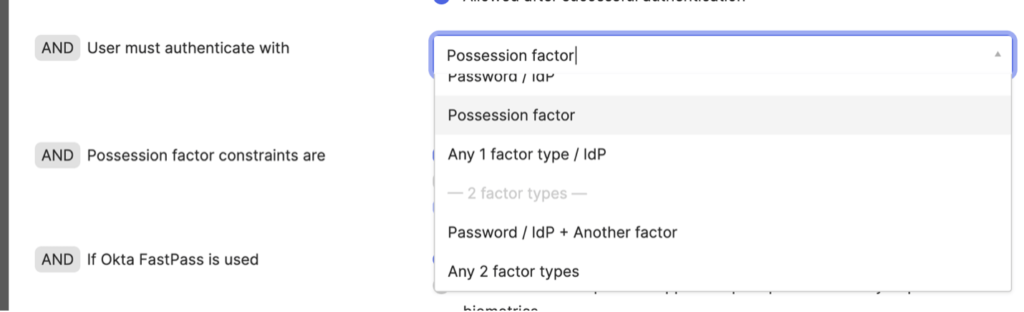
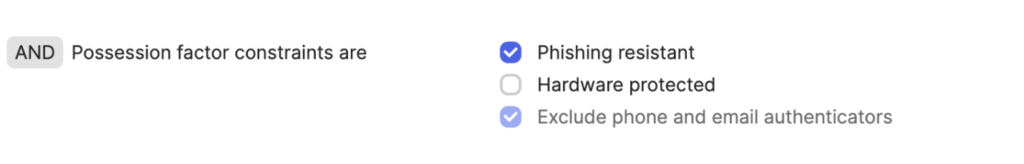
Additionally, you can enforce the types of possession factor MFA you want to accept. Traditional OTPs and pushes to a registered mobile device are susceptible to phishing attempts. Enforcing FIDO2 (i.e. YubiKey) or certificate-based authentication (PIV/CAC) are ways to protect your organization from phishing attacks.
Additionally, OIE introduced a new authentication method called FastPass. Okta FastPass is agent-based (you install the Okta Verify app on your device) and transparently uses certificate-based authentication to authenticate users without the use of passwords. It integrates with Windows Hello and MacOS TouchID, so you can require biometric authentication (making it password-less multifactor authentication!)

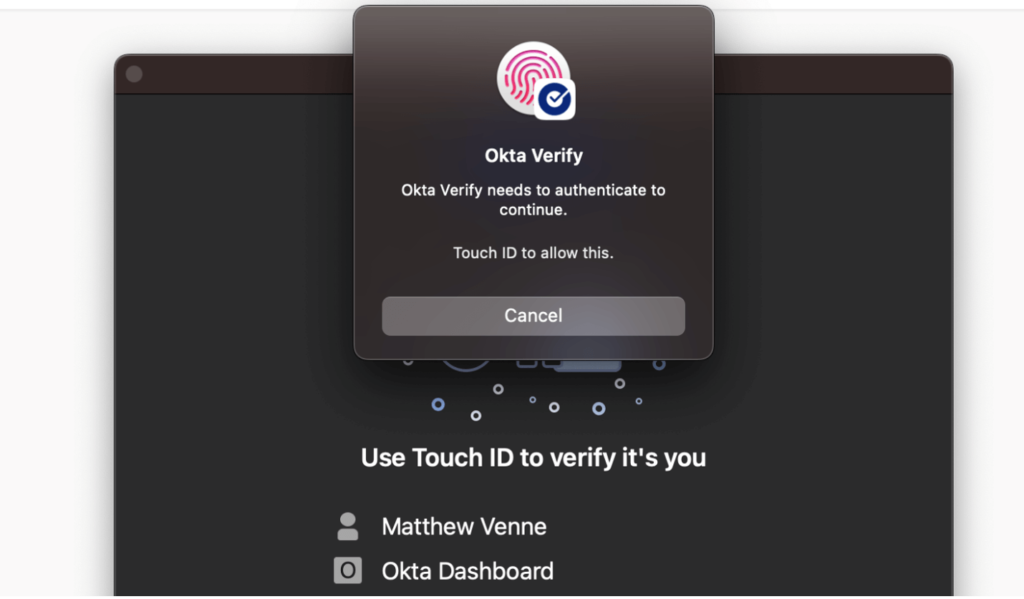
Context-Aware Access:
One of the core tenants of Zero trust is authenticating the devices used by users as well as their identities. Using an unapproved device to access a network could make an organization susceptible to data leaks. OIE considers various contextual factors when granting access. It considers the user’s location, device health, network conditions, and the sensitivity of the resource being accessed. If any of these factors raise suspicions, access can be denied or subjected to further authentication. Additionally, when Okta FastPass is used for authentication, it can be configured to only allow access if the user’s device is managed by your corporate endpoint management solution.
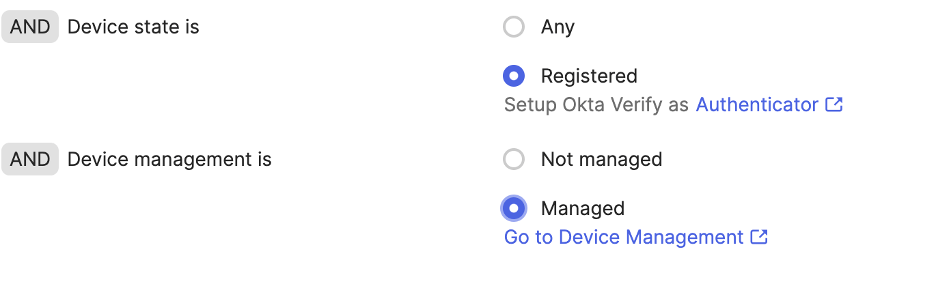
While this requires additional configuration with your endpoint management solution, this would prevent users from accessing the sensitive data from unapproved devices.
Risk-based authentication / Continuous Monitoring: Zero Trust is not a one-time check but an ongoing process. Okta’s Identity Engine continuously monitors user and device behavior, looking for unusual or suspicious activities. It uses machine learning to track a user’s behavior over multiple sessions. It associated a risk-based score based on this data and this can be used to further craft your authentication policies. The recent hack of major casinos like MGM is a great example of where this went wrong. While Okta was used as the Identity Provider in those hacks, the initial vector used by the attackers was phishing – where the attacker called the casino’s IT support and asked to have an admin’s multifactor authentication method reset so they can re-enroll it to a device owned by the attacker. While this could be seen as a policy/procedure failure, compromise could have been avoided by configuring OIE to restrict or block application access entirely from new devices and new locations (i.e., High risk).

Note: Device authentication could have prevented this hack as well since the attacker would not have had a device managed by the casino.
Single Sign-On (SSO): By integrating all your applications with OIE, you offer your users a better experience since they only need to have one set of credentials to authenticate. Additionally, if all users are going through Okta for authentication, it allows you to centralize the security policy enforcement of the users.
Conclusion:
It’s clear to see that Information security is a complex and always evolving. However, that’s why it’s important to continuously evaluate your security stack against new solutions that are emerging. These new solutions are usually based off the latest threat models developed by security professionals. This is certainly the case with Okta’s Identity Engine. It’s interpretation of zero trust principles and how they are implemented are specifically designed to protect you against the newest threat vectors.
Okta is an integral part of stackArmor’s ThreatAlert® ATO Accelerator for FedRAMP, FISMA and CMMC 2.0 compliance.

