Providing cloud solutions to government agencies requires those cloud solutions to hold a Fedal Risk and Authorization Management Program (FedRAMP) Authorization to Operate (ATO). There are 2 paths to obtaining a FedRAMP ATO: Sponsorship by an Agency and a provisional ATO (P-ATO) through the Joint Authorization Board (JAB). This blog will cover the path to ATO through an agency sponsor since agency ATOs account for 70 percent of all FedRAMP ATOs. JAB PATOs will be covered in a separate blog.
1 – Find an agency willing to sponsor the cloud service offering (CSO).
Finding an agency to sponsor and champion a Cloud Service Offering (CSO) through the FedRAMP process is probably the longest pole in the tent for getting the coveted FedRAMP Authorization. The issuance of an agency ATO represents an acceptance of risk associated with the CSO on the part of the agency’s authorizing official (AO).A prime candidate for this authorization route is an agency that is currently using or wanting to use the CSO, and is therefore motivated to invest in/commit to the FedRAMP authorization process. This potential sponsor could be any government agency, sub-agency, department, and/or other government entity that has the ability/bandwidth and willingness to sponsor the solution. To formalize the sponsorship process, the agency will submit a formal Letter of Sponsorship to the FedRAMP Project Management Office (PMO). Once approved, the Cloud Service Provider (CSP) will be listed in the FedRAMP Marketplace under the FedRAMP “In Process” designation.
2 – Identify a dedicated FedRAMP team and trusted compliance advisor.
FedRAMP is a significant undertaking, with widespread organizational impacts. Pursuing an ATO without an experienced, trusted compliance advisor will likely end with less-than-desirable results for a CSP. The FedRAMP authorization process can be convoluted, complex, and difficult to navigate even for a seasoned compliance professional. The time and money saved in reducing the number of “didn’t-you-knows”, “do-overs” and “back-to-the-drawing-boards” will more than cover the cost of a trusted advisor well-versed in FedRAMP who can shepherd a CSP through the process.
3 – Engage a 3rd Party Assessment Organization (3PAO).
CSOs are required to be assessed by an accredited, independent 3PAO as a part of the FedRAMP authorization process. Given the growing backlog of CSPs pursuing FedRAMP and other compliance authorizations, it’s best for a CSP to establish a relationship with a 3PAO early. This gives the 3PAO time to align resources and reserve a place on their busy schedules for the assessment work. Establishing the relationship early will also let the sponsoring agency know there is an understanding of and reasonable commitment to the authorization process on the part of the CSP.
4 – Determine the appropriate control baseline for the CSO.
With FedRAMP, like NIST, there are 3 possible baselines for any CSO. The required baseline depends on the potential impact of a breach of a CSO’s data integrity, confidentiality and/or accessibility as determined by FIPS 199 impact level criteria. Those impact levels result in the following baselines, each with a pre-defined set of required cybersecurity controls:
- Low Baseline[1] (125 Controls for NIST Rev 4, 150 for NIST Rev 5)
Covers low-risk, non-mission-critical CSOs with data intended for public use. Data loss wouldn’t compromise an organization’s mission, safety, finances, or reputation. - Moderate Baseline (325 Controls for NIST Rev 4, 304 for NIST Rev 5)
Covers CSOs that include data that is not publicly available, such as personally identifiable information (PII). A breach of this data could have a potentially serious impact on operations. - High Baseline (421 Controls for NIST Rev 4, 392 for NIST Rev 5)
Covers CSOs that include sensitive federal information such as, law enforcement, emergency services, and/or healthcare data. Breaches could be catastrophic – potentially threatening safety, operations, financial viability, or human life.
5 – Shore up technical readiness and consider inherited controls.
Before embarking on a full assessment by a 3PAO, CSPs need to perform a technical assessment and gap analysis, identifying potential showstoppers to a FedRAMP authorization. Once the formal authorization process begins, a CSP has twelve (12) months to obtain an ATO without having to re-visit the agency sponsorship commitment. While a discussion of all technical requirements could fill up a short book, ensuring all external systems and services have an existing FedRAMP ATO that is equal to or higher than the authorization level being pursued by the CSO, and that all data at rest and in transit within the system and among leveraged services is encrypted using FIPS 140-2 (soon to be 140-3) validated modules are two of the biggest issues that are non-negotiable and considered to be showstoppers. The easiest way to shore up gaps and reach a state of compliance is to leverage FedRAMP authorized cloud infrastructure/platform-as-a-Service (IaaS/PaaS) service providers (e.g., Amazon Web Services, Microsoft Azure, etc.), whose compliant controls can be inherited and leveraged by the CSO.
6 – Navigate the agency authorization process.
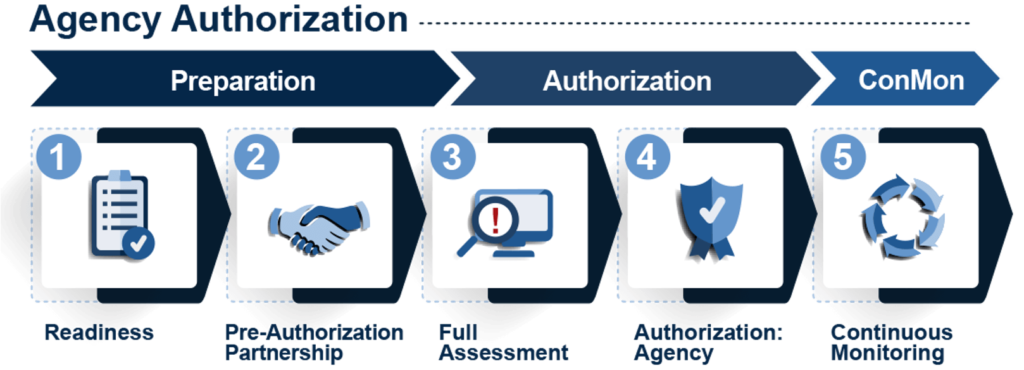
The Figure below highlights the key steps and milestones that move a CSO through the authorization process, which is overseen by the sponsoring agency in collaboration with the FedRAMP PMO.).
- Readiness – A formal Readiness Assessment conducted by an accredited 3PAO, and Readiness Assessment Report (RAR) are not required for most agencies. A Readiness Assessment can be used by an agency to determine the overall readiness of a CSO to undergo a Full Assessment. The Readiness Assessment focuses on areas of security mandated by the FedRAMP PMO and performs a high-level review of each of the required control families as well as the state of the CSO’s required documentation. A CSO does not have to be 100% finalized to undergo a Readiness Assessment, but it must be able to demonstrate alignment with key FedRAMP security requirements.
- Pre-Authorization Partnership – As discussed, partnering with a sponsor is required for for CSPs that seek an agency-sponsored FedRAMP authorization path. CSPs must understand and address their specific sponsor’s ATO requirements.
- Full Assessment – A full assessment must be conducted by a 3PAO. A CSO is required to be operating in a compliant state for a minimum of 90 days, as evidenced by monitoring logs, before a full assessment should begin. Additionally, an extensive set of FedRAMP-specific documentation, including policies and procedures, a system security plan (SSP), a contingency management plan, etc., will need to be created. Upon completion of the initial Full Assessment, the authorization package: System Assessment Plan (SAP), System Assessment Report (SAR); SSP; and Plan of Action and Milestones (POA&M); is submitted to the agency.
- Agency Authorization – Upon reviewing the authorization package and working with the 3PAO and CSP to address any shortcomings, an agency will grant an ATO. Once the ATO is issued by the agency, the authorization package is then submitted to the FedRAMP PMO for final review and formal FedRAMP Authorization. Upon FedRAMP Authorization, that ATO package can then be re-used by other agencies to grant their own ATO, preventing the CSP from being required to go through the full assessment process each time.
- Continuous Monitoring – An ATO is just the beginning. foundational to compliance is the ongoing ConMon activities that include daily, monthly, quarterly and annual activities, with deliverables that must be submitted on an ongoing basis to both the AO and FedRAMP PMO.
7 – Continuous Monitoring Services.
Continuous monitoring is a requirement to maintain a FedRAMP Authorization , with change control processes, incremental vulnerability scanning and status reporting to the AO all being required activities. These activities are highly structured and control-driven and call for compliance-trained Security Operations Center (SOC) operators.
ConMon reports and significant change requests must be communicated to and, where necessary, approved by the sponsoring agency AO throughout the life of the agency-sponsored ATO. Additionally, each authorized system must be reassessed by a 3PAO on an annual basis.
About stackArmor
stackArmor helps commercial, public sector and government organizations rapidly comply with FedRAMP, FISMA/RMF, DFARS and CMMC compliance requirements by providing a dedicated authorization boundary, NIST compliant security services, package development with policies, procedures and plans as well as post-ATO continuous monitoring services.
[1] FedRAMP currently has two baselines for systems with Low Impact data: LI-SaaS Baseline and Low Baseline. The LI-SaaS Baseline accounts for Low-Impact SaaS applications that do not store personal identifiable information (PII) beyond that generally required for login capability (i.e. username, password, and email address). Required security documentation is consolidated and the requisite number of security controls needing testing and verification are lowered relative to a standard Low Baseline authorization. Additional information on requirements for the LI-SaaS baseline can be found on the FedRAMP Tailored website.