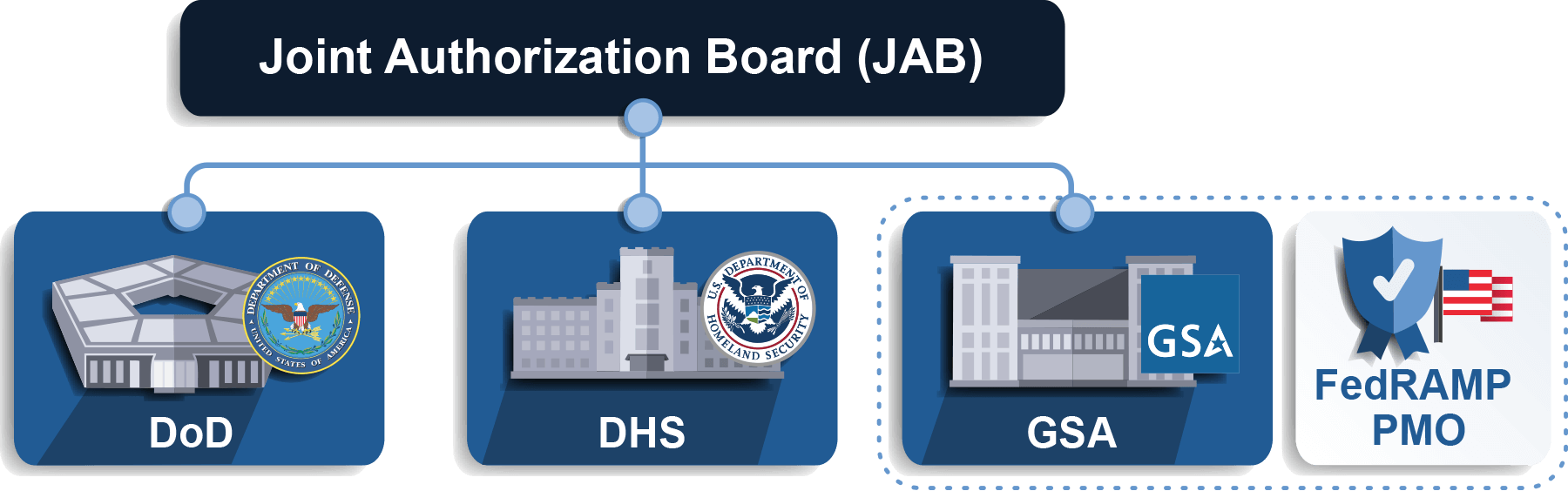
In a previous Blog, stackArmor reviewed the process of obtaining an agency sponsored Federal Risk and Authorization Management Program (FedRAMP) Authority to Operate (ATO). Any cloud service provider (CSP) serving government agencies must have a FedRAMP Authorization. This blog will address the second, less common path to obtaining a FedRAMP Authorization: through a Joint Authorization Board (JAB) sponsorship. The JAB is FedRAMP’s primary governing body whose board includes Chief Information Officers (CIOs) from the following three federal organizations:
- Department of Defense (DoD)
- General Services Administration (GSA)
- Department of Homeland Security (DHS)
A JAB authorization is slightly different than an agency authorization as it results in a Provisional ATO (P-ATO). It is provisional because the JAB cannot accept risk on behalf of any agency, only an agency can do that with their ATO. Agencies are still able to access and use the available P-ATO package to grant their own ATO, making it just as reusable as an agency ATO.
1 – Prepare for the JAB authorization process.
There are many steps a CSP should take before beginning a FedRAMP journey. While many of these are similar to an agency sponsorship, there are some key differences.
- Onboard a trusted compliance advisor – Pursuing a FedRAMP Authorization is a significant undertaking, regardless of the path chosen. Initiating the effort without an experienced, trusted compliance advisor is likely to end with less-than-desirable outcomes. The cost of a compliance advisor who is well-versed not only in FedRAMP but with the JAB process itself will be a smart investment that will pay dividends for a CSP in the long run.
- Determine the cloud service offering’s (CSOs) target controls baseline – There are three possible baselines for a CSO seeking JAB authorization. The required baseline depends on the potential impact of a breach of a CSO’s data integrity, confidentiality and/or accessibility as determined by FIPS 199 impact level criteria. Those impact levels result in the following baselines, each with a pre-defined set of required cybersecurity controls: .
- Low Baseline (125 Controls for NIST Rev 4, 156 for NIST Rev 5)
For low-risk, non mission-critical systems with data intended for public use. Data loss wouldn’t compromise an organization’s mission, safety, finances, or reputation. Moderate Baseline (325 Controls for NIST Rev 4, 323 for NIST Rev 5)
Covers CSOs that include data that is not publicly available, such as personally identifiable information (PII). A breach of this data could have a potentially serious impact on operations. - High Baseline (421 Controls for NIST Rev 4, 410 for NIST Rev 5)
Covers CSOs that include sensitive federal information such as, law enforcement, emergency services, and/or healthcare data. Breaches could be catastrophic – potentially threatening safety, operations, financial viability, or human life. - Align to JAB tech standards and consider inherited controls – Before embarking on a 3rd Party Assessment Organization (3PAO) assessment, CSPs should perform their own technical assessment to identify gaps and showstoppers to FedRAMP Authorization. This analysis and alignment should be guided by a trusted advisor that understands JAB security controls and requirements around the system’s authorization boundary.
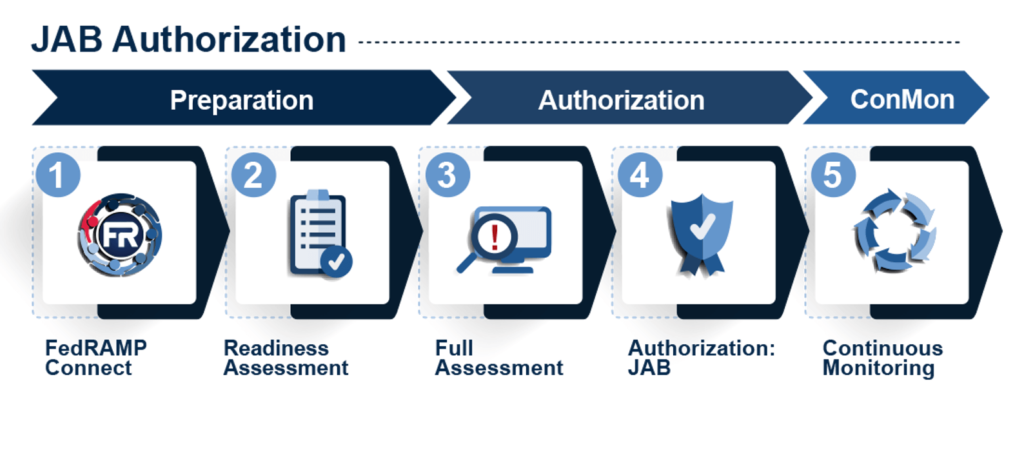
2 – Engage a 3PAO for a JAB Readiness Assessment.
Cloud systems are required to be assessed by an accredited 3PAO twice to obtain a JAB ATO: once to achieve “FedRAMP Ready” status in accordance with JAB standards, and another time to complete a full authorization assessment. The Readiness Assessment is not explicitly required for an agency sponsored ATO. A CSP must be “FedRAMP Ready” in accordance with JAB standards within 60 days of being prioritized (selected) by the JAB. Since it is unlikely that a 3PAO readiness assessment can be completed and approved by the JAB PMO in 60 days, the assessment should be started, if not completed, before or in conjunction with pursuing a JAB authorization.
3 – Apply for JAB Sponsorship through FedRAMP Connect.
Due to the JAB’s limited resources and commitment to sponsor CSOs with government-wide value, a CSP seeking a JAB P-ATO must apply for consideration through FedRAMP Connect – which involves a standardized, criteria-based analysis of each CSO that guides prioritization based on two factors: demand and desirability.
- Demand – CSPs must complete a Business Case using the FedRAMP PMO template showing government-wide need for the CSO. A scoring Rubric ensures a standardized and objective selection process, and considers evidence such as existing federal customers, commercial cloud customers, or federal customers using an on-prem version of the CSO.
- Desirability – CSOs must show evidence of features or capabilities that meet high priority government needs such as addressing regulatory requirements or filling identified gaps in existing government software stacks. As an example of a solution that is likely to be prioritized, a CSO that delivers supply chain security or zero trust architecture elements would have desirable features with respect to the latest executive order, EO 14028, on Improving the Nation’s Cybersecurity.
4 – Navigate the JAB authorization process.
The JAB process, like the agency process, follows key steps and milestones to move a CSO from readiness through authorization and into ConMon. Unlike the agency process however, where any one of many agencies may sponsor, the JAB’s limited resources mean they can only sponsor approximately 12 CSPs each year.
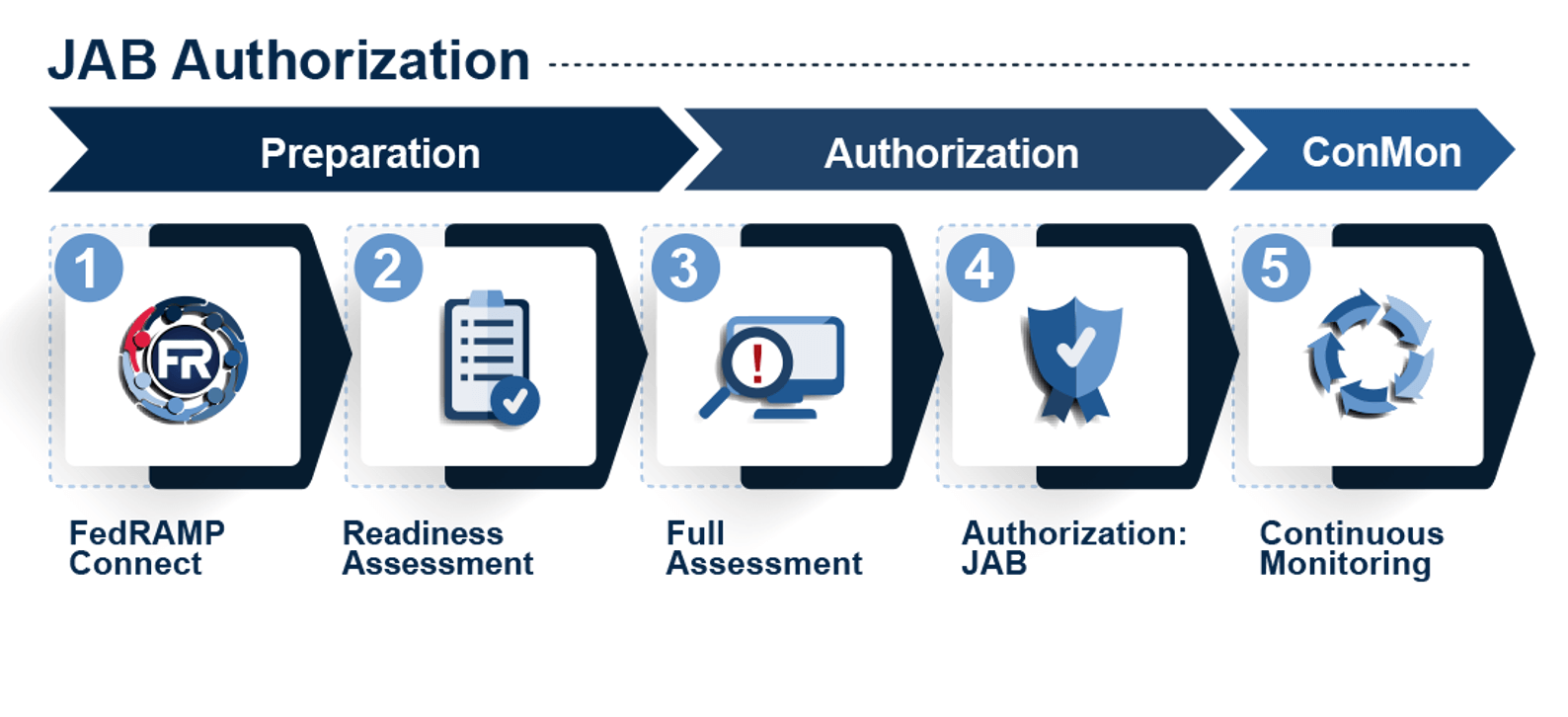
- FedRAMP Connect – As discussed above, CSPs must apply for JAB sponsorship consideration using the FedRAMP Connect process.
- “JAB Ready” Readiness Assessment –A Readiness Assessment Report (RAR) must be completed within 60 days of being selected, by an accredited 3PAO prior to full assessment. The RAR documents the CSO’s capability to meet federal security mandates and the overall security requirements of the FedRAMP control baseline.
- Full Assessment – After a “FedRAMP Ready” designation is achieved, a full assessment must be conducted by the 3PAO. Upon completion, the authorization package: System Assessment Plan (SAP), System Assessment Report (SAR); System Security Plan (SSP); and Plan of Action and Milestones (POA&M); is submitted to the JAB PMO for review.
- JAB Authorization –Once an assessed system has been found to meet the JAB’s criteria, a P-ATO will be granted and the CSO will be listed in the FedRAMP marketplace as Authorized.
- Continuous Monitoring – Once Authorized, ongoing ConMon activities shall include daily, monthly, quarterly and annual actions and deliverables that are to be provided to the JAB in accordance with the FedRAMP PMO ConMon Guidance.
ConMon reports and significant change requests will be communicated to, and where necessary, approved by the JAB throughout the life of the JAB-sponsored P-ATO. Additionally, each authorized CSO must be reassessed by a 3PAO on an annual basis.
About stackArmor
stackArmor helps commercial, public sector and government organizations rapidly comply with FedRAMP, FISMA/RMF, DFARS and CMMC compliance requirements by providing a dedicated authorization boundary, NIST compliant security services, package development with policies, procedures and plans as well as post-ATO continuous monitoring services.