Security and compliance-focused customers especially delivering services to Government organizations must comply with FedRAMP, FISMA, or CMMC requirements. NIST SP 800-53 establishes baseline security requirements that define continuous monitoring controls. Specific controls and security families that drive information system monitoring and reviewing auditable events include SI-4 and AU-2d as representative examples:
| No. | Control Name | Control | Description | Frequency |
| 1 | Information System Monitoring | SI-4 | Monitors the system in accordance with SI-4 control requirements | Continuous/ Ongoing |
| 2 | Auditable Events | AU-2d | Monitor required events | Continuous/ Ongoing |
Amazon Web Services (AWS) continues to evolve the security services portfolio and recently released AWS Security Hub for centralized security incident reporting and management. AWS Security Hub gives a comprehensive view of your high-priority security alerts and security posture across your AWS accounts. With Security Hub, you now have a single place that aggregates, organizes, and prioritizes your security alerts, or findings, from multiple AWS services, such as Amazon GuardDuty, Amazon Inspector, Amazon Macie, AWS Identity and Access Management (IAM) Access Analyzer, and AWS Firewall Manager, as well as from AWS Partner solutions. It also generates its findings as to the result of running automated and continuous checks against the rules in a set of supported security standards. These checks provide a readiness score and identify specific accounts and resources that require attention. Security Hub is SOC, ISO, PCI, and HIPAA certified.
Benefits of Using AWS Security Hub as a Centralized Incidents and Events Store
– Consolidated view of findings across AWS accounts and providers: It provides a consolidated view of the security findings across AWS accounts and providers and displays results on the Security Hub console. The consolidated view enables identifying potential issues and taking necessary remediation steps.
– Reduced effort in collecting and prioritizing findings: Security Hub processes findings data using a standard findings format, thereby, eliminating the need to manage findings data from multiple formats. It then correlates findings across providers to prioritize the most important ones.
– Automated security checks to ensure compliance with best practices: Security Hub automatically runs continuous, account-level configuration, and security checks based on AWS best practices and industry standards.
– Ability to automate remediation findings: Security Hub supports integration with Amazon CloudWatch Events. To automate the remediation of specific findings, you can define custom actions to take when a finding is received.
Building a Robust Security Management System
As organizations grow and continue to store sensitive information ranging from business intelligence to personally identifiable information, health records, credit cards, and other regulated data in the cloud, having a cloud security strategy is extremely critical. It is certain that the cloud is here to stay and that security professionals need to put a continuous emphasis on threats and vulnerabilities detection and management processes and systems. Security operations or SecOps is a team of expert individuals responsible for monitoring and analyzing an organization’s security posture on an ongoing basis. The SecOps helps detect, analyze, and respond to cybersecurity incidents using a combination of technology solutions and a strong set of processes. Security operations monitor and analyze activity on networks, servers, endpoints, databases, applications, websites, and other systems, aiming to identify anomalous activity that could be a security incident or compromise. The NIST CSF, NIST SP 800-53, and FedRAMP are key reference points for standards, guidelines, and best practices for managing the threat lifecycle.
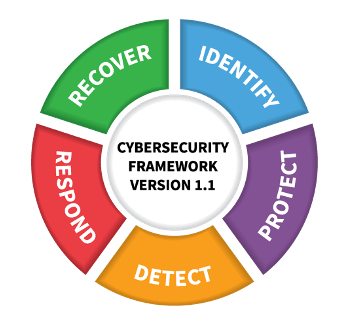
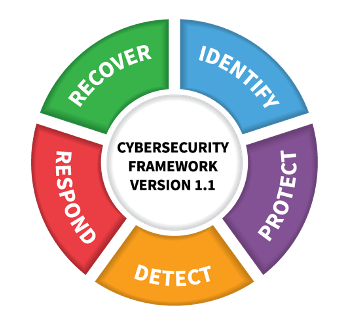
Figure 1: The NIST Cyber Security Framework
Security operations or SecOps is a team of expert individuals responsible for monitoring and analyzing an organization’s security posture on an ongoing basis. The SecOps helps detect, analyze, and respond to cybersecurity incidents using a combination of technology solutions and a strong set of processes. Security operations monitor and analyze activity on networks, servers, endpoints, databases, applications, websites, and other systems, aiming to identify anomalous activity that could be a security incident or compromise. The NIST CSF, NIST SP 800-53, and FedRAMP are key reference points for standards, guidelines, and best practices for managing the threat lifecycle.
The NIST recommends the following key activities:
Identify: Assess your environment and gain a complete understanding of your people, physical, and digital assets, risks, and vulnerabilities, and defense systems
Protect: Establish a layered and diverse approach to combating threats and vulnerabilities
Detect: Implement technologies and practices to enable quick detection of threats and potential attacks
Respond: Ability to respond appropriately to an incident and protect it from becoming a serious breach
Recover: Ability to return to its original state by planning for resilience and implementing preventive measures to safeguard against a repeat attack
Organizations looking to simplify and streamline their security events collections and response capabilities can increasingly rely on cloud-native services like AWS Security Hub to avoid costly third-party software.
About stackArmor
As an AWS Security Competency Partner, stackArmor specializes in FedRAMP, FISMA, and DFARS compliance on AWS and AWS GovCloud for Commercial, Non-Profit, and Public Sector Organizations. Our cloud engineers can deploy and configure AWS Security tools into your AWS environment and provide ongoing management support as per your needs. As part of the Authority to Operate (ATO) on AWS partner program, stackArmor offers a Cloud GSS (security system) called stackArmor ThreatAlert® that is specifically tailored to meet NIST SP 800-53 security requirements on AWS and AWS GovCloud. The stackArmor ThreatAlert® solution is a continuous monitoring and security incident and vulnerability monitoring solution for AWS cloud services. It offers an in-boundary FedRAMP compliant landing zone with an integrated security system meeting NIST SP 800-53 security control requirements including FIPS 140-2 compliant remote access, MFA authentication and authorization, boundary protection, continuous monitoring, and Security Incident Event Management (SIEM), and segmentation for production data. Have questions? Click here to contact us for a free demo of the stackArmor ThreatAlert® solution.