Commercial ISV’s and SaaS providers looking to provide cloud-based services to US Federal and Department of Defense customers must be accredited by obtaining a FedRAMP P-ATO (Authority to Operate). The FedRAMP accreditation program is based on the NIST SP 800-53 Rev 4 security and compliance framework that specifies controls, policies and procedures. Every commercial cloud service provider must demonstrate the ability to ensure the confidentiality, integrity and availability of government data. The FedRAMP P-ATO is based on the data sensitivity associated with the platform and offers Low-Impact SaaS (LI-SaaS), Low, Moderate or High baselines based on FIPS 199 standards.
Amazon Web Services (AWS) offers a FedRAMP accredited solution that offers a wide variety of native services that help accelerate the compliance process by allowing Commercial ISV’s and SaaS providers meet the rigorous security standards. It is critical to select and leverage the right sets of service components and develop a compliant architecture that meets NIST SP 800-53 prescribed security control families and standards.
A critical requirement to meeting FedRAMP certification standards is strong network protection, access management and control. Traditional solutions have relied on Virtual Private Network (VPN) technology to securely connect to the Amazon Web Services (AWS) infrastructure for remote access. However, there are a number of challenges and issues that arise by providing access at the network layer that require additional segmentation, access controls and monitoring services that increase costs and complexity. Zscaler Private Access (ZPA) is a VPN-alternative that recently received FedRAMP accreditation and is available for Commercial ISV’s to leverage to simplify their remote access solution.
Using Zscaler Private Access to Provide Secure Role-Based Access to your AWS Cloud
As many organizations across the globe adopt a Cloud-First strategy, the need for stream-lined role-based access to vital resources becomes a higher priority.
How does Zscaler Private Access work?
- ZPA is offered as a virtual appliance, called Zscaler Connectors, that act as the gateway into your AWS environment. They do not require a public IP; they only require internet access thru a NAT device and port 443 over TLS to the Zscaler Cloud. They are easily clustered for high availability and load balancing. Deployment is under 10 minutes via a Community AMI. Zscaler connector’s do not factor into license procurement at all; you only pay for the AWS EC2 compute costs. Additionally, since it is a virtual appliance, Zscaler manages all patching and software updates for you! The required ingress data transfer for patching is minimal.
- You explicitly define your applications in Zscaler’s web-based Admin console. You could can group each application in application segments, and then group application segments for coordinating access. Each IP/Port definition is considered an application (this is important for licensing).
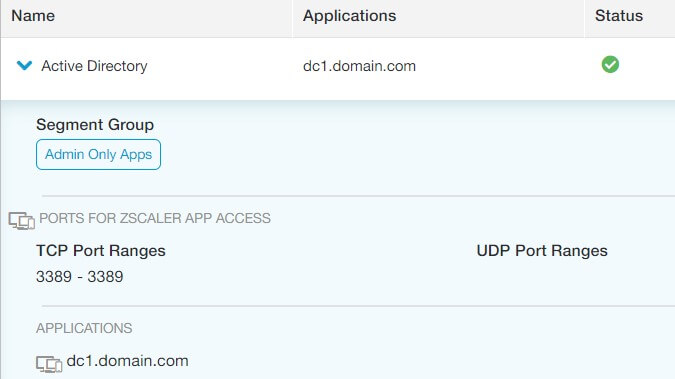
- You can also define web applications for Private Access also. Accessing these applications can be done directly in the browser with no VPN client. After defining the web application in the console, you just need to create a CNAME in your corporate DNS provider that points the FQDN of your web application to Zscaler’s cloud (since they broker the connector). Zscaler provides the exact alias target when creating the definition.
That’s great, but how do I grant access?
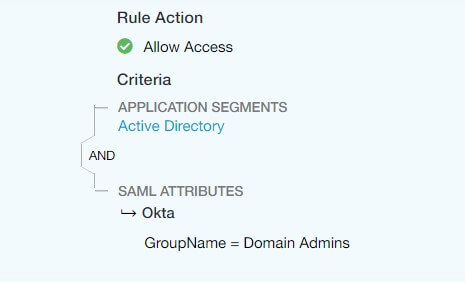
- Zscaler integrates with any SAML 2.0 provider such as Okta, DUO, and Active Directory Federation Services.
- Configure your SAML provider to forward certain attributes about your users, such as AD security group, department, office location, name etc.
- Then in the Zscaler Admin Console, you can create Access Policies. In each access policy, you define what applications you want a subset of users to access. Then you can define which user attributes have access to the segments defined in this application segment. So, if you only want your IT department to be able to access a particular application segment, you could set your SAML provider to forward the department attribute to Zscaler. Upon authentication, Zscaler would then check that attribute and if the department value = IT, they would be granted access to that application segment. If their department value = HR, then they would be granted to the resources defined in that access policy (if there is no access policy for HR, then they would not be able to access anything!)
- Additionally, Zscaler Access policies allow you to define if you want this access policy to grant access via the Browser (client-less), or via using ZAPP, Zscaler’s VPN client (which is required for RDP, SSH, and other protocols required for non-browser access). This is great if you want to provide users access to a web application, but only want privileged users to access the underlying OS, while only defining one application segment.
This is exciting! How does licensing work?
- Zscaler licensing depends on 3 variables:
- # of users who will be using Zscaler private applications,
- the # of applications (remember 1 IP/Port is an application),
- whether or not you require a FedRAMP environment for compliance reasons.
- There two licensing options:
- Professional – 4 defined applications or less. No custom health reports, or device posture (basically, make sure any connecting client device meets a security baseline such as Anti-Virus or domain-joined)
- Business- up to 10,000 applications and includes device posture and health reports.
stackArmor is excited to be working with security and compliance focused customers looking to implement FedRAMP compliant cloud solutions that help reduce the time and cost by using pre-defined solution architecture components. Contact us to learn more.
Learn more about our FedRAMP compliance solutions by visiting our ATO on AWS solutions page at https://stackarmor.com/solutions-2/devops/
