FedRAMP, FISMA and DFARS mandates for Government and Department of Defense focused systems must implement Multi-Factor Authentication as a key requirement. US Federal agencies, Public sector organizations, Educational institutions and Government contractors must comply with NIST SP 800-53 or NIST SP 800-171 requirements, Multifactor authentication is a key security component. Luckily, using FedRAMP accredited services like Amazon Web Services (AWS) and DUO make this relatively easy to implement.
About Multi-Factor Authentication
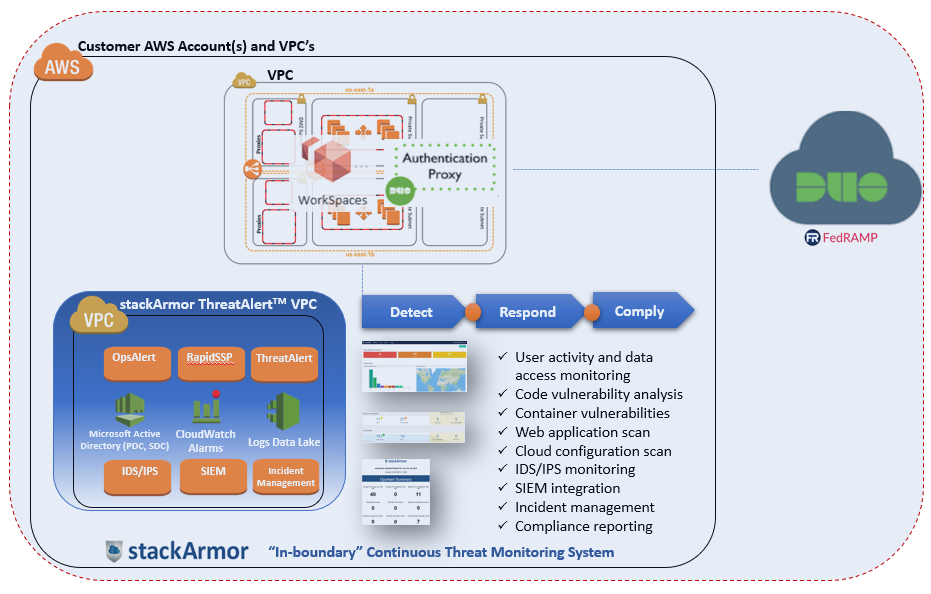
Multi-factor authentication is a key security component that provides an added layer of security to applications and systems. Stronger authentication achieved by using two different forms of authentication are needed to login (usually a password and a TOTP on your phone). This ensures that even if one method of authentication is compromised, the attacker will not be able to login to the system or application. Furthermore, MFA is required to be compliant with different standards such as HIPAA, NIST, FEDRAMP, DFARS 252.204-7012 etc. We recently had an opportunity to implement a NIST SP 800-171 compliant system to help a Defense contractor comply DFARS 252.204-7012. The developed solution included the following key components:
- AWS GovCloud accredited at FedRAMP High level
- Amazon WorkSpaces in GovCloud Region
- stackArmor ThreatAlertTM – FedRAMP GSS (General Security System) for meeting continuous monitoring and compliance controls
- DUO
For organizations looking to comply with NIST SP 800-171 or NIST SP 800-53 requirements for multi-factor authentication, here’s a short tutorial on how to use as DUO as an MFA service in AWS GovCloud.
Step 0:
Setup AWS GovCloud account and configure basic services including VPC’s etc and set up Amazon WorkSpaces and the Microsoft Active Directory (AD) service. Login to the AD and create users for the Amazon WorkSpaces and spin up the Amazon WorkSpaces for those users. Make sure you add the same users as DUO users or add the AD name to the alias of this user on DUO.
Step 1:
Login to the Duo Admin portal and navigate to the Applications tab.
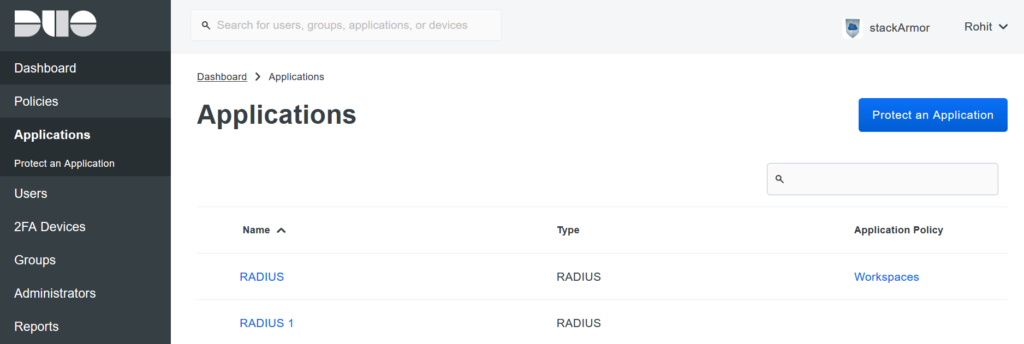
Step 2:
Choose ‘protect an application’ and look for the application called RADIUS.
Step 3:
Once you choose RADIUS, keep track of the integration key, secret key and API hostname, scroll down to Global policy for new users and set it to ‘Deny access’, this is needed as workspaces expects a deny from the MFA provider.
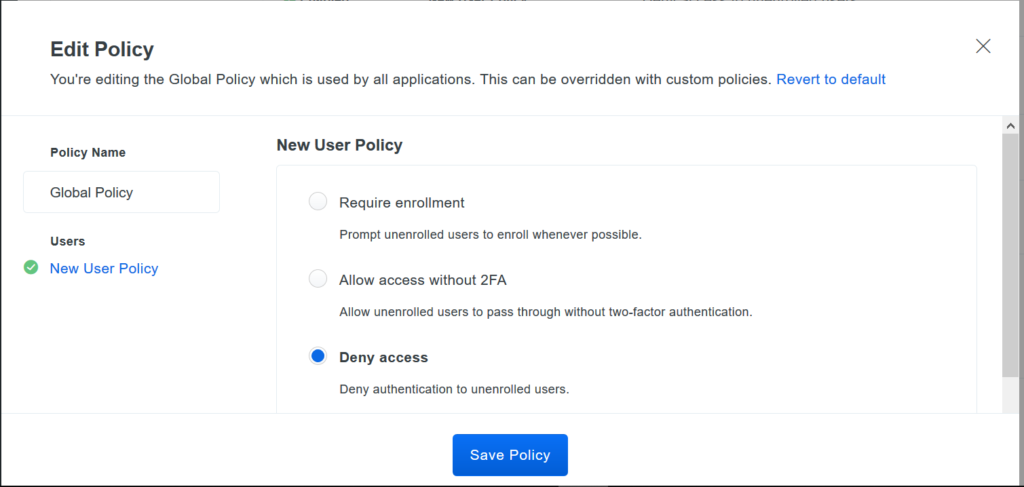
Step 4:
Install the DUO authentication proxy on the instance you want to act as the RADIUS server.
Windows – https://dl.duosecurity.com/duoauthproxy-latest.exe.
Step 5:
Navigate to the conf file under ‘install directoryconfauthproxy.cfg’ and create a stanza similar to the following:
[duo_only_client]
[radius_server_duo_only]
ikey=DIXXXXXXXXXXXXXXXXXX
skey=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
api_host=api-XXXXXXXX.duosecurity.com
failmode=safe
radius_ip_1=x.x.x.x
radius_secret_1=theradiussecret
radius_ip_2= x.x.x.x
radius_secret_2=theradiussecret
port=1812
Where ikey,skey and api_host are from the DUO admin panel and the radisu_ips are ip addresses of your domain controllers.
And ensure you restart the DUO service by using the ‘net stop DuoAuthProxy & net start DuoAuthProxy’command on CMD.
Step 6:
Now navigate to the AWS console’s directory service, then to the Networking and security tab and click on enable MFA and fill-in the details with the information up until this point. Ensure you adjust the security groups to allow communication the RADIUS port.
Step 7:
Once the MFA setup is done, test to see if the Workspaces Client prompts for the MFA code as shown below.
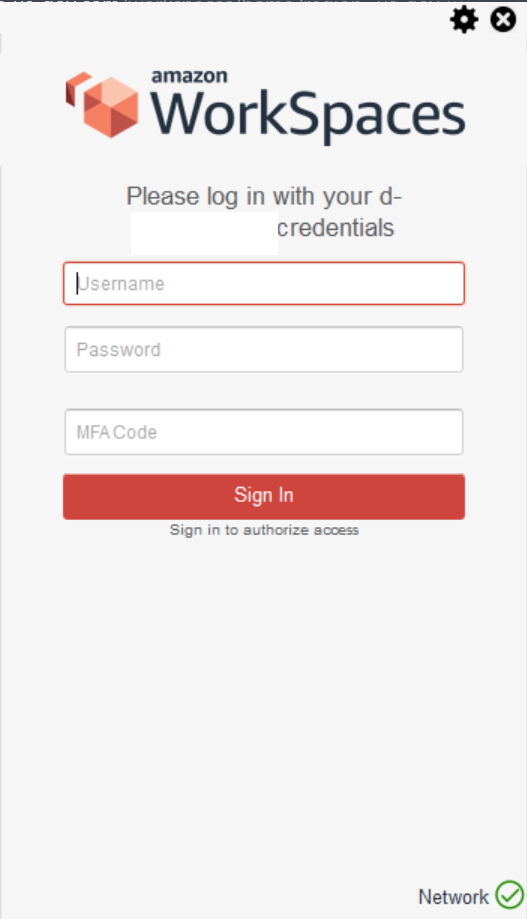
We hope this helped. Please let us know if you have any questions at solutions at stackArmor dot com or learn more about our Government cloud solutions by visiting https://www.stackArmor.com/GovernmentCloud


