The Change Healthcare security breach has impacted over 94% of hospitals as reported by the American Health Association (AHA). A cascading set of events was unleashed starting with the Feb 21, 2024 announcement of the data breach at Change Healthcare requiring nearly $2B in advance payments severely impacting nearly 900,000 physicians, 33,000 pharmacies, 5,500 hospitals and 600 laboratories. The security attack is reported to have been caused by a security vulnerability in software provided by ConnectWise and used by Change Healthcare.
Security and cybersecurity incidents in healthcare are not new. However, what makes the Change Healthcare security breach standout is the widespread impact and the need for a forceful government response that included the Whitehouse. In many ways this cyberattack mirrors the Colonial Pipeline incident a few years ago where Citizens faced gas shortages serving as a wakeup call to policy makers that cybersecurity incidents can be disruptive to the economy in ways not well understood before.
As agencies and congress start to investigate and analyze what happened and how to avoid such event in the future, it is important to consider what works and what has not worked.
Ineffective Voluntary Cybersecurity Regulation and Enforcement?
Cybersecurity regulation in the United States has largely been voluntary with a patchwork of regulators, weak cybersecurity standards and lack of real enforcement. Both NIST and CISA have tried for many years to assist and help with improving the cybersecurity posture by providing free resources. The hope being that a voluntary regime would allow markets to make the right investments. Civil lawsuits, fines or risk transfer mechanisms through cybersecurity insurance have been used as measures to deal with cybersecurity risks especially in critical infrastructure sectors.
However, in over a decade of trying the voluntary or “market-based” cybersecurity model, serious cybersecurity breaches continue to happen with increasing frequency and economic reach. The day to day lives of citizens are being adversely impacted. As Congress and the Whitehouse look for solutions, it is important to consider new regulatory models to drive change and effect meaningful change. The Federal Risk Assessment and Management Program (FedRAMP) provides a template that can inform future cybersecurity regulatory approaches based on a decade of data.
Is it time for HealthRAMP and Authority to Operate (ATO) for Healthcare?
The FedRAMP Program was established in 2011 and codified into law in 2022. The program is credited with enabling the induction of commercial cloud services in a secure and safe manner. FedRAMP is considered the gold standard in cybersecurity. There are three characteristics that differentiate this program from all other cybersecurity standards:
- A strong no-nonsense government regulator
- Systemic view of cybersecurity that includes the supply chain
- An uncompromising continuous monitoring and enforcement program
As Congress looks to find solutions, it is important to review and consider the FedRAMP intent, structure, and outcomes to drive change in healthcare cybersecurity. Developing a strong cybersecurity regulatory framework is especially important as artificial intelligence is just around the corner and it is critical to protect users and the economy from cybershocks.
Developing “FedRAMP Lite” that is funded by Industry but Regulated by a Federal Agency?
Since the establishment of the FedRAMP program in 2011, there have been several relevant variations and models that can satisfy both industry’s desire for an efficient cybersecurity regulatory model and the government’s need to ensure a safe and secure digital economy. The StateRAMP program is operated by a non-profit and is focused on helping states and local government agencies. The StateRAMP program builds upon FedRAMP. Using a variation of that playbook, HealthRAMP can be funded and setup like the FINRA – Financial Industry Regulatory Authority, which is a not-for-profit organization that oversees U.S. broker-dealers.
FINRA is funded by industry and is overseen by the SEC. HealthRAMP could be incorporated similarly and use the same security standards and processes that have been successful at delivering secure cloud services to US Public sector and defense agencies since 2011. Healthcare industry members would be responsible for paying a fee and must maintain their Authority to Operate (ATO) through a formal and mandatory assessment & accreditation regime. For example, if Change Healthcare wanted to use ConnectWise software then both would have to obtain a HealthRAMP ATO at the level data security classification level.
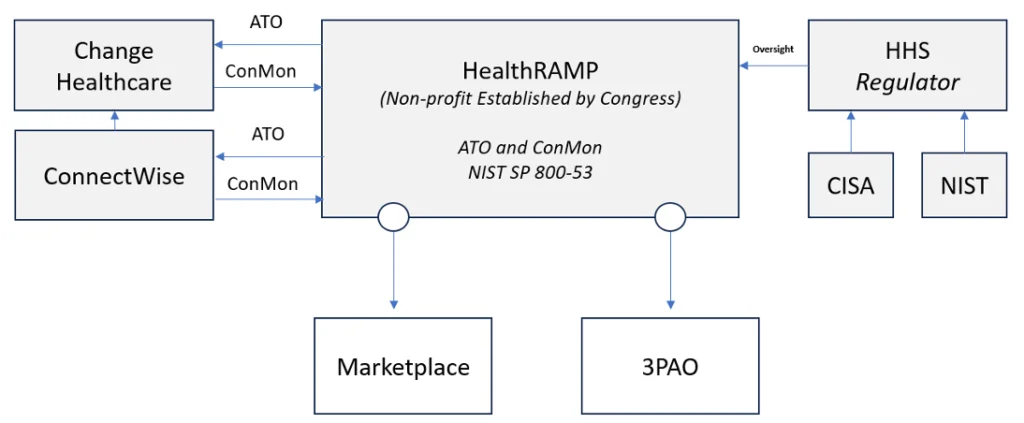
The HealthRAMP Model for Managing Cybersecurity Risk in Healthcare based on the FedRAMP Program.
Evolving the cybersecurity regulatory framework based on lessons from the past can inform our path forward. The success and rigor associated with NIST SP 800-53 controls, use of government supervised regulatory bodies and a uncompromising continuous monitoring program are essential ingredients for a effective solution.
