stackArmor has developed a holistic cloud cybersecurity assessment, architecture and operations framework that is based on real-world implementation experience with US Federal Agencies, Department of Defense, and large Financial and Security-focused Commercial organizations. Given the increased need for cybersecurity oversight and compliance, organizations are seeking to find the fastest path to complying with ISO 27001, HIPAA, FISMA, FedRAMP, FFIEC or NIST standards. We provide highly tailored and outcome focused cybersecurity consulting services to help organizations perform gap assessments, tools evaluation, benchmarking and security architecture reviews. Our team of cloud security and compliance experts support FedRAMP, FISMA, CMMC, HIPAA, SOC2 and PCI-DSS frameworks especially on AWS and AWS GovCloud regions. Our offerings are described in greater detail below.
Security Review Report
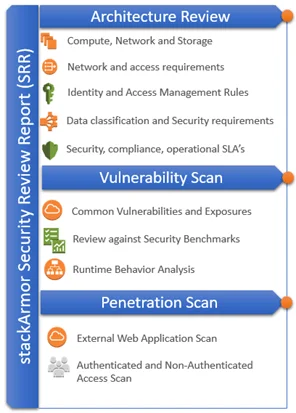
stackArmor has developed the Security Review Report (SRR) artifact as a first step for organizations to assess their risk posture for AWS cloud based workloads and applications. The Security Review Report covers three major technology focused components of a cloud-based environment that includes:
– Review of the architecture of the hosting environment
– An internal vulnerability scan of the hosting environment and finally
– An external penetration scan of the hosting environment.
The infographic shows how a full-stack architecture review typically consists of the environment, application(s), data, operating system and the cloud platform that must be protected. The actual current state of the security state is assessed by reviewing the structure, evaluating the software on the platform and the external exposure and threat surface available for attacks from the outside. The stackArmor Security Review Report (SRR) is a great light-weight starting point for organizations trying to assess their security posture.
Architecture Review
Creating a robust and secure architecture on AWS EC2 requires understanding core principles that ensure that the hosting environment is secure and robust to meet business and security standards for online systems. The architecture review consists of the following key elements:
– Access management and control through means such as VPN, SSH, Bastion host, RDP or similar means to ensure that privileged users such as administrators and developers are securely accessing the environment.
– Segmentation of the various layers of the application including using Application or Elastic Load Balancers (for public facing sites), private sub-nets for web servers, separate security groups and subnets for database servers and services.
– Data protection policies including the use TLS/https for encrypting data in motion including reviewing TLS termination end points. Using AES-256 encryption for data at rest in EBS volumes or S3 buckets. Reviewing database encryption especially of sensitive data fields.
– Continuous Monitoring configuration and setup through the use of cloud-native services such as Amazon CloudWatch, CloudTrail, Config, Macie and external services such as Splunk.
– High-availability and fault tolerance using Multiple-Availability Zones, and architecting for redundancy.
Misconfigurations Scan
AWS cloud services need to be configured to ensure that security best practices are followed. Given that a lot of organizations may not be familiar with some of these best practices, stackArmor performs a scan of the configuration and setup using the EC2 API’s and covers key services to detect potential misconfigurations. The stackArmor ThreatAlert® scan reviews the various settings and configurations of AWS components and services.
Vulnerability Scan
The internal vulnerability scan is performed using tools to help identify presence of vulnerabilities as reported to the NIST’s CVE database by various vendors. Tools such as Amazon Inspector, Tenable Nessus or OpenSCAP are commonly used to detect such vulnerabilities. The findings are grouped into Critical, High, Medium and Low’s. The best practice is to remediate Critical and High. With a plan of action to remediate Medium’s and Low’s. It is very common for such vulnerabilities to show up in the system due to delays in applying patches that typically includes a yum update for Linux systems or a WSUS update for Windows. AWS services such as Amazon EC2 Systems Manager provides a native patching solution that provide a systematic solution.
Penetration Testing
An external penetration scan helps identify vulnerabilities in the exposed web application. Typically, this scan is performed in anonymous mode and authenticated mode. The penetration scan helps detect issues such as SQL injection, XSS, click-jacking and other common web application related vulnerabilities. The penetration scan is typically performed using tools such as Tenable Nessus or Metasploit amongst others.
For large organizations seeking to implement a strong security and governance model for cloud-systems, we have developed a light-weight and highly agile framework called ARM (Assess, Remediate and Monitor).

The Assessment phase begins with the creation of a risk model and conducting a gap analysis to understand the current state. The risk model identifies the risk factors (threats, vulnerabilities, impact, likelihood, and predisposing conditions) to be assessed and defines the relationships among them.
A threat is any circumstance or event with the potential for adverse impact to operations, assets, or personnel. The source of a threat can be human, environmental, or a structural failure and may be intentional or accidental in nature.
A vulnerability is a weakness in an information system, security procedure, internal control, or implementation that may be exploited by a threat source.
A predisposing condition is a condition that exists within the organization, its business processes, enterprise architecture, or operating environment that affects the likelihood that initiated threat events result in an adverse impact.
The likelihood of occurrence is a weighted risk factor based on the probability that a given threat is capable of exploiting a given vulnerability.
The impact of a successful exploitation of a vulnerability or predisposed condition is a measure of the magnitude of harm that could be expected to the firm, its assets, or personnel.
The assessment approach combines the measurable aspects of a traditional quantitative assessment with the flexibility of a qualitative assessment. This provides meaningful risk results that allow for prioritization. In order to provide improved rigor and effectiveness of risk analysis, a vulnerability-oriented analysis with an impact-oriented analysis to provide a more complete risk picture that identifies vulnerabilities in policy, process, and technology as well as critical assets and the impact of successful attacks against those assets.
The Assessment phase includes a comprehensive review of policies, procedures, practices and tools currently deployed within the enterprise. The environment is scanned for detecting vulnerabilities using penetration testing and scanning tools that are NIST compliant and includes web applications and operating systems software for identifying patching levels.
Based on the findings of the Assessment, a remediation activity is conducted that is commensurate with the organization’s desired security posture. Typically, the remediation phase includes providing a Basic Security Policy that provides an initial baseline.
As part of the remediation activity, a Security Assessment Report (SAR) is created that summarizes the scope, approach, high level findings and recommendations. Typically, organization create a Plan of Actions and Milestones (POAM) to implement the recommendations. Findings are categorized as High, Medium or Low. The general practice is to remediate all High’s and a significant number of the Medium’s.
Once all remediation activity is concluded, Automated scans with basic parameters are executed to ensure that vulnerabilities have actually been addressed.
Given the dynamic nature of the hosting and software environment, it is critical to ensure that continuous operational activities for vulnerability management, continuous monitoring and executive management reviews are conducted on a periodic basis, preferably monthly but at least quarterly.
An annual penetration and vulnerability test should be conducted to ensure a stable baseline. stackArmor has implemented a continuous monitoring and compliance verification service to help organizations easily establish baselines and assess their risk.
Click here to learn more about stackArmor ThreatAlert.
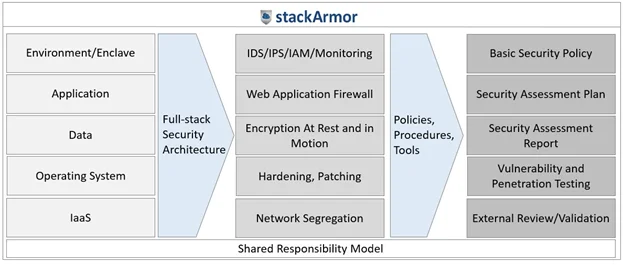
Coupled with the right framework and governance methodology, it is critical to have a full-stack security architecture that covers and protects the entire stack including the environment, application, data and infrastructure. Each element of the architecture requires its own set of tools to protect from the threat vectors for that specific layer. Finally, in addition to the tools, relevant policies and procedures must be incorporated to provide a holistic cybersecurity solution. The diagram provides a high-level overview of the full-stack framework:
Related Content:
Have questions about vulnerability assessment? Are you interested in a Free Consultation with a stackArmor Security Architect on how you can secure your cloud systems from vulnerabilities, meet HIPAA, FFIEC, FedRAMP, or FISMA compliance requirements? We can help you review your workload requirements, and also assist with your security and compliance needs. Schedule a free consultation with a stackArmor DevOps Solutions Architect by sending us an email at solutions@stackarmor.com.
stackArmor, Inc. a Tyto Athene Company, provides FedRAMP, FISMA/RMF, and CMMC/DFARS compliance acceleration services. stackArmor’s ThreatAlert® Security Platform reduces the time and cost of an ATO by 40%. We serve enterprise customers in Defense, Aerospace, Space, Government, and Healthcare markets as well as ISV’s looking to offer cloud solutions for Government.
Menu
© stackArmor. All Rights Reserved 2025.