The State of California has enacted the California Consumer Privacy Act of 2018 that goes into effect on Jan 01, 2020. The Act has many provisions that will impact the cybersecurity and data management capabilities for any organization with data about California residents. The California Consumer Privacy Act of 2018 also has clear guidelines on consumer rights in the event of a data breach. The language from the Act is reproduced below.
1798.150. (a) (1) Any consumer whose nonencrypted or nonredacted personal information, as defined in subparagraph (A) of paragraph (1) of subdivision (d) of Section 1798.81.5, is subject to an unauthorized access and exfiltration, theft, or disclosure as a result of the business’ violation of the duty to implement and maintain reasonable security procedures and practices appropriate to the nature of the information to protect the personal information may institute a civil action for any of the following:(A) To recover damages in an amount not less than one hundred dollars ($100) and not greater than seven hundred and fifty ($750) per consumer per incident or actual damages, whichever is greater.(B) Injunctive or declaratory relief.(C) Any other relief the court deems proper.
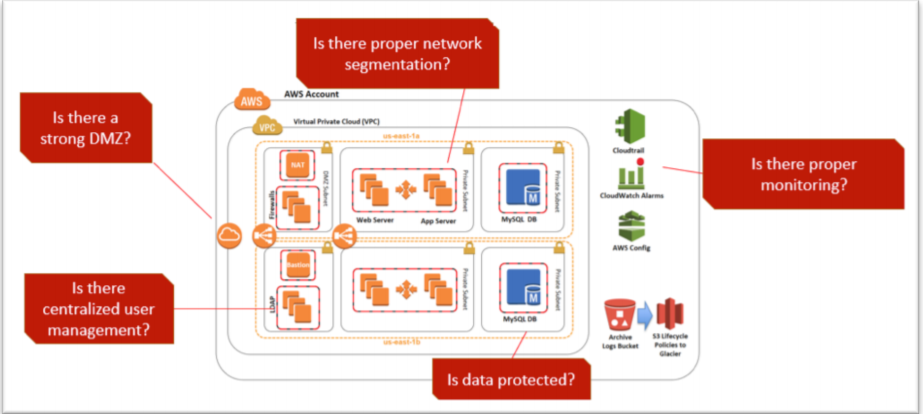
Clearly, there is an increasing regulatory response to poor cybersecurity and privacy practices in digital organizations. In order to rapidly comply with security and privacy regulations, cloud computing services like Amazon Web Services (AWS) offer a set of ready to use tools and services to implement security best practices and secure consumer data. AWS offers multiple tools and technologies to encrypt data and avoid common vulnerabilities. The cybersecurity and compliance experts at stackArmor have develop a security best practices playbook that identifies focus areas to help create a secure hosting environment.
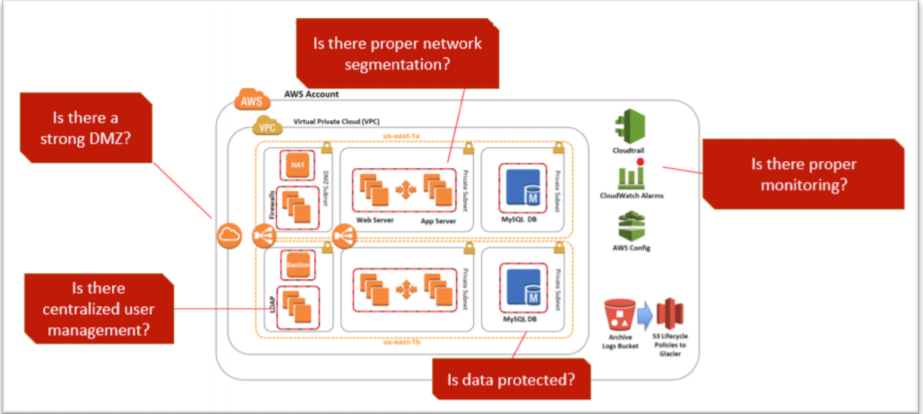
Avoiding penalties related to data loss requires implementing strong data encryption and monitoring capabilities. AWS offers multiple data encryption solutions.
- Develop a zero-trust security framework that encrypts data in motion both outside and inside the AWS VPC. Most organizations remember to use https for external communication but often do not encrypt internal communications between the application server and database server as an example. Encrypting all data in motion should be a default practice.
- Creating a holistic data at rest encryption policy is essential and should include all forms of storage including backups in Amazon Glacier, S3 buckets and EBS volumes. AWS offers AES-256 bit encryption of out the box that is relatively easy to use. Advanced users should consider key management solutions and leverage BYOK (bring your own key) services the KMS (Key Management Service) provided by AWS.
- Encrypting databases is often overlooked. Data at rest encryption helps protect data on disk. AWS RDS offers a number of easy to use encryption features. Users must remember that planning encryption polices ahead of time is critical – not all RDS instance types support encryption and encryption can only be selected during the initial create phase. However, it is important to remember to protect sensitive data inside the database as well. Transparent Data Encryption (TDE) can be used with encryption at rest, to provide a comprehensive data protection scheme especially for sensitive user information.
Regulations like California Consumer Privacy Act of 2018, GDPR, HIPAA, FedRAMP, FISMA or PCI-DSS all have a common goal of helping drive the adoption of security and privacy best practices. As organizations look for ways to find cost efficient and secure ways to void vulnerabilities in their systems, it is critical to adopt a Security by Design posture. If you are an organization looking to get a headstart on compliance with California Consumer Privacy Act of 2018 then do contact us for a free security assessment.
Learn more about our security review report.
https://stackarmor.com/vulnerability-management-and-penetration-testing-on-aws-cloud/